For the past decade, the cybersecurity industry has rallied behind a single, catchy slogan: “Shift Left.”
The logic seemed impeccable. If we move security testing earlier in the software development lifecycle (SDLC), from the final staging phase “left” into the coding phase, we can catch bugs cheaper, faster, and more effectively. On PowerPoint slides presented in boardrooms across the world, this looked like a win-win. Security teams would stop being bottlenecks, and developers would be empowered to own the quality of their code.
But in 2026, the reality on the ground tells a different, darker story.
For many organizations, “Shift Left” didn’t mean shifting responsibility or capability; it meant shifting blame. We took complex enterprise security tools, originally designed for specialized analysts, and dumped them onto the laptops of overworked developers who were already struggling to meet aggressive shipping deadlines.
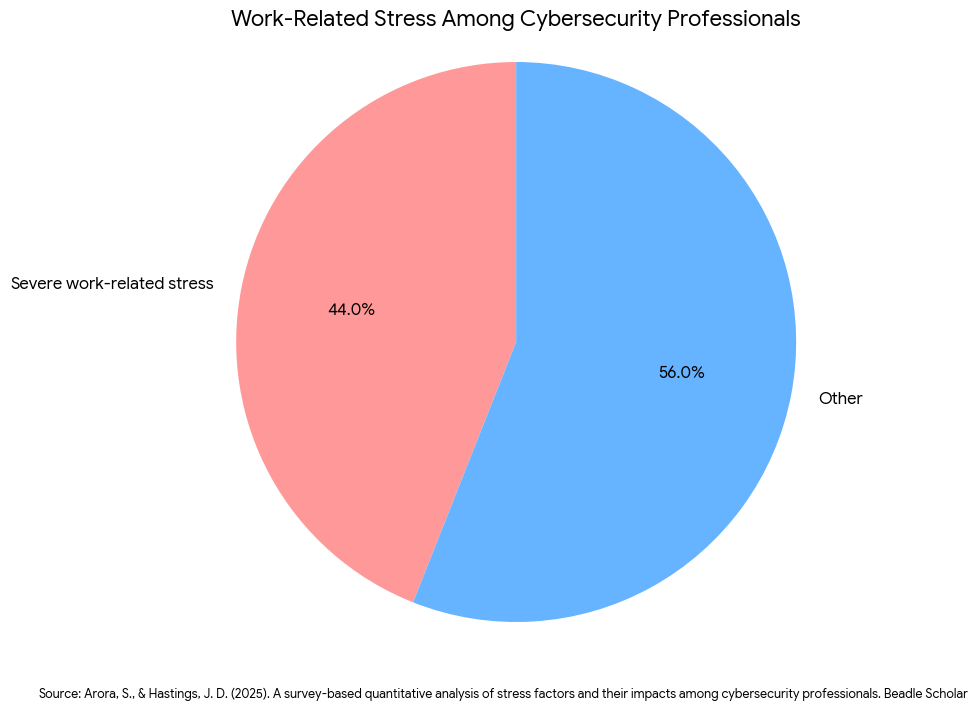
The result isn’t a more secure codebase. The result is “alert fatigue,” massive friction between teams, and a silent crisis of burnout. According to the 2024 study A Survey-Based Quantitative Analysis of Stress Factors and Their Impacts Among Cybersecurity Professionals1 from Dakota State University, 44% of cybersecurity practitioners report experiencing “severe” work-related stress. This data validates the industry consensus that unrealistic expectations are fueling a crisis of resilience. Sustainable defense cannot be built on unsustainable workloads.
To fix this, we need to stop lying to ourselves about what “Shift Left” has become. We must replace the failed strategy of “developer heroism” with a new model of “platform engineering.” It is time to stop asking developers to be part-time security analysts and start giving them an environment where the secure way is the only way.
The Friction Point: Why “Shift Left” Failed
The failure of the traditional Shift Left model stems from a fundamental misunderstanding of the modern developer’s cognitive load.
In a cloud-native world, a “full-stack developer” is already expected to understand microservices, container orchestration, database schemas, and front-end frameworks. When we add “vulnerability management” to that list without proper integration, we break the workflow.
Data from the Black Duck 2025 DevSecOps Report reveals the extent of this friction: 53% of organizations report that application security tools significantly slow down their development pipelines. Even more telling, while 60% of organizations are now releasing software daily, nearly half (46%) still rely on manual processes to onboard new projects into security testing.
This creates a paradox. We demand speed (DevOps) while introducing speed bumps (Security). When a developer commits code and immediately receives a PDF report listing 300 “Critical” vulnerabilities, most of which are false positives or irrelevant to their specific context, they don’t fix them. They ignore them. They view security not as a partner, but as a tax on their productivity.4
This is where the distinction between “scanning” and “management” becomes vital. As detailed in Emutare’s guide to the Integration of Vulnerability Management with DevOps,2 true integration is not about running a scan every time a developer hits “save.” It is about intelligent orchestration. It requires systems that can differentiate between a vulnerability in a library that is actually loaded in production versus one that is dormant. It requires automated ticketing that sends the right fix to the right person, rather than blasting a generic alert to the entire team.
Without this intelligence, “Shift Left” is just noise.
The Solution: “Shift Smart” via Platform Engineering
If we can’t train every developer to be a security expert, and we can’t hire enough security analysts to check every line of code, what is the solution?
The answer lies in a burgeoning trend that Gartner identified as a top strategic technology for 2025: Platform Engineering.5
Instead of asking developers to manually configure security tools, organizations are building “Internal Developer Platforms” (IDPs). These are self-service portals that allow developers to spin up infrastructure that is pre-approved and pre-secured.
Think of it as a “Golden Path.” If a developer wants to deploy a new microservice, they don’t start from scratch. They use a template provided by the Platform Engineering team. This template already has the correct IAM (Identity and Access Management) roles, the approved encryption standards, and the required logging agents installed.
This approach fundamentally changes the dynamic. We aren’t asking the developer to “build securely”; we are giving them a “secure building block.”
This aligns perfectly with the principles of Privacy by Design: Implementation Framework for Modern Organizations.3 Privacy by Design argues that privacy and security should be the default setting, not an optional toggle. In a Platform Engineering model, the default setting for any new database is “encrypted.” The default setting for any API is “authenticated.” The developer would have to go out of their way to make it insecure. By shifting the security controls into the platform layer (the infrastructure), we remove the cognitive burden from the application layer (the code).
This is “Shift Smart.” The security happens before the developer even writes a single line of business logic.
The Role of Automation and AI
The rise of AI has further complicated, and potentially solved, parts of this puzzle.
According to the GitLab 2025 Global DevSecOps Report,4 97% of respondents say they are currently using or plan to use AI in their software development lifecycle. While this adoption accelerates coding, it introduces new risks such as ‘vibe coding’ (using AI prompts without understanding the output), which 73% of respondents cite as a cause of code quality issues, creating a need for Platform Engineering to bridge the gap between speed and security
In the old “Shift Left” model, a tool would tell a developer: “Error: SQL Injection vulnerability found on line 45.” The developer then had to research what that meant and how to fix it.
In the new AI-driven model, the platform says: “SQL Injection found. Here is a generated Pull Request that parameterizes the query to fix it. Click here to merge.”
This is the holy grail of developer experience. It transforms security from a “problem spotter” into a “solution provider.” When security tools actually help developers finish their tickets faster (by fixing bugs for them), the cultural antagonism evaporates.
However, we must be careful. Automation is not a silver bullet. If we automate bad processes, we just generate errors faster. The underlying architecture must be sound. This requires a rigorous application of the vulnerability management lifecycle, assess, prioritize, act, integrated into the CI/CD pipeline, as emphasized in the Integration of Vulnerability Management with DevOps article.
Re-Engineering the “Human Firewall”
Even with the best platforms and AI, the human element remains.9 Developers are creative problem solvers; if a security control blocks them, they will find a workaround.
This brings us to the cultural aspect of the solution. We need to stop training developers using the same generic “Phishing Awareness” slides we show to the HR department. Developers face unique threats, supply chain attacks, secret leakage, and API manipulation, and they need unique training.
Most developers actually want to write secure code; they just lack the specific knowledge or the time to do so. A “Just-in-Time” training approach is far more effective than annual compliance seminars. This means delivering a 2-minute micro-lesson on “Cross-Site Scripting” exactly when a developer tries to commit code containing that vulnerability.
This contextual learning is a core tenant of effective Security Awareness Program Design: Beyond Compliance.5 By treating developers as high-value assets who need specialized coaching rather than “users who need policing,” we build trust.
External research supports this targeted approach. A landmark study titled “The Compliance Budget: Managing Security Behaviour in Organisations“6 found that employees possess a finite mental capacity for adhering to security protocols. Researchers discovered that compliance effectively collapses once the “friction cost” of a rule exceeds a user’s available budget, causing them to prioritize productivity over unexplained security hurdles.
The “Guardrails, Not Gates” Manifesto
To successfully fix the broken “Shift Left” promise, organizations should adopt a “Guardrails, Not Gates” philosophy.
A “Gate” is a stopper. It is a security review that happens 48 hours before launch, threatening to delay the release. Developers hate gates. Business leaders hate gates.
A “Guardrail” is a continuous boundary. It is the linter in the IDE (Integrated Development Environment) that highlights a hard-coded password in red as it is being typed. It is the automated policy that prevents an S3 bucket from being made public. Guardrails guide the developer toward safety without stopping the car.
Implementation Steps for Leaders
- Audit Your Toolchain: Look at the security tools you are forcing developers to use. Do they integrate into VS Code and GitHub, or do they require logging into a separate portal? If it’s the latter, get rid of them.
- Invest in Platform Engineering: Stop hiring more “AppSec Engineers” to nag developers. Hire “Platform Engineers” to build secure templates for developers.
- Measure “Mean Time to Remix”: Don’t just measure how many bugs you find. Measure how long it takes a developer to fix them. If that number is high, your tools are failing the developer.
Conclusion
The “Shift Left” movement was born from good intentions, but it lost its way. We tried to make security everyone’s job, and in doing so, we made it no one’s priority.
The future of secure software delivery isn’t about shifting more work onto the developer. It is about shifting the complexity away from them and into the platform. It is about using automation, AI, and architectural guardrails to create an environment where speed and security are not enemies, but allies.
Developers don’t hate security. They hate friction. Remove the friction, and you will find that your developers are the best security champions you never knew you had.
Is your “Shift Left” strategy creating developer burnout? Emutare helps you build the “Golden Path” to secure delivery without the friction. We provide intelligent vulnerability management to cut through alert fatigue and AI-driven process automation to streamline your pipeline. Our expert software development services assist in constructing the secure platform infrastructure your teams need, while our targeted awareness training empowers developers instead of policing them. Stop demanding heroism and start enabling speed with security. Partner with Emutare to make “Shift Smart” a reality for your organization today.
References
- Arora, S., & Hastings, J. D. (2025). A survey-based quantitative analysis of stress factors and their impacts among cybersecurity professionals. Beadle Scholar. https://scholar.dsu.edu/cgi/viewcontent.cgi?article=1221&context=ccspapers ↩︎
- Emutare. (2025). Integration of Vulnerability Management with DevOps. https://insights.emutare.com/integration-of-vulnerability-management-with-devops/ ↩︎
- Emutare. (2025). Privacy by Design: Implementation Framework for Modern Organizations. https://insights.emutare.com/privacy-by-design-implementation-framework-for-modern-organizations/ ↩︎
- GitLab. (2025, November 10). GitLab survey reveals the “AI paradox”: Faster coding creates new bottlenecks requiring platform solutions. https://about.gitlab.com/press/releases/2025-11-10-gitlab-survey-reveals-the-ai-paradox/ ↩︎
- Emutare. (2025). Security Awareness Program Design: Beyond Compliance. https://insights.emutare.com/security-awareness-program-design-beyond-compliance/ ↩︎
- Beautement, A., Sasse, M. A., & Wonham, M. (2009). The compliance budget: Managing security behaviour in organisations. Proceedings of the 2008 New Security Paradigms Workshop, 47–58. https://dl.acm.org/doi/epdf/10.1145/1595676.1595684 ↩︎
Related Blog Posts
- Board Reporting on Cybersecurity: What Executives Need to Know
- Multi-Factor Authentication: Comparing Different Methods
- Secrets Management in DevOps Environments: Securing the Modern Software Development Lifecycle
- Zero Trust for Remote Work: Practical Implementation
- DevSecOps for Cloud: Integrating Security into CI/CD
- Customer Identity and Access Management (CIAM): The Competitive Edge for Australian Businesses
- Infrastructure as Code Security Testing: Securing the Foundation of Modern IT

