Why consolidation, visibility, and forensic readiness are the new metrics for financial resilience in the age of AI
For years, the relationship between the Chief Financial Officer and the Chief Information Security Officer (CISO) has been defined by a difficult tension. The CISO asks for more budget to combat rising threats, and the CFO asks a question that is becoming harder to answer: “If we are spending more every year, why do we not feel safer?”
It is a valid question. In the current economic climate, where efficiency is paramount, the “black hole” of cybersecurity spending is under the microscope. The traditional approach — buying a new tool for every new threat- has reached a point of diminishing returns. It has created a bloated, complex infrastructure that is expensive to maintain and, ironically, easier for attackers to breach.
The path forward for 2025 and beyond is not necessarily to spend less, but to spend differently. It requires shifting from a strategy of “volume” to one of “visibility.” By understanding the hidden costs of tool sprawl, the silent liability of shadow data, and the financial risks of AI-driven fraud, finance leaders can partner with IT to build a security posture that protects the bottom line as effectively as it protects the network.
The High Cost of Complexity
The most significant drain on the modern security budget is not the cost of the threats themselves, but the cost of the tools purchased to stop them. Over the last decade, organizations have accumulated dozens, sometimes hundreds, of disparate security applications. This phenomenon, known as “tool sprawl,” creates a fragmented environment where data is trapped in silos.
As we explored in The “Tool Sprawl” Trap: Why More Security Tools Can Mean Less Security,1 this complexity incurs a “tax” on your security operations. You are paying for overlapping licenses, multiple support contracts, and the excessive man-hours required to make these systems talk to each other.
The market is waking up to this inefficiency. This trend is best summarized by Microsoft’s findings on vendor efficiency, as stated in its How Microsoft Security partners are helping customers do more with less.2 Their data reveals that the average customer can cut their security bill by 60% simply by eliminating the overlap inherent in a multi-vendor environment. For the modern CFO and CISO, this turns security consolidation into a clear financial correction: it allows the organization to retire expensive legacy point solutions and redirect those funds toward actual threat defense rather than vendor management. By consolidating vendors, organizations can reduce the “management overhead” of security, the time analysts spend switching between dashboards, and redirect those resources toward proactive threat hunting.
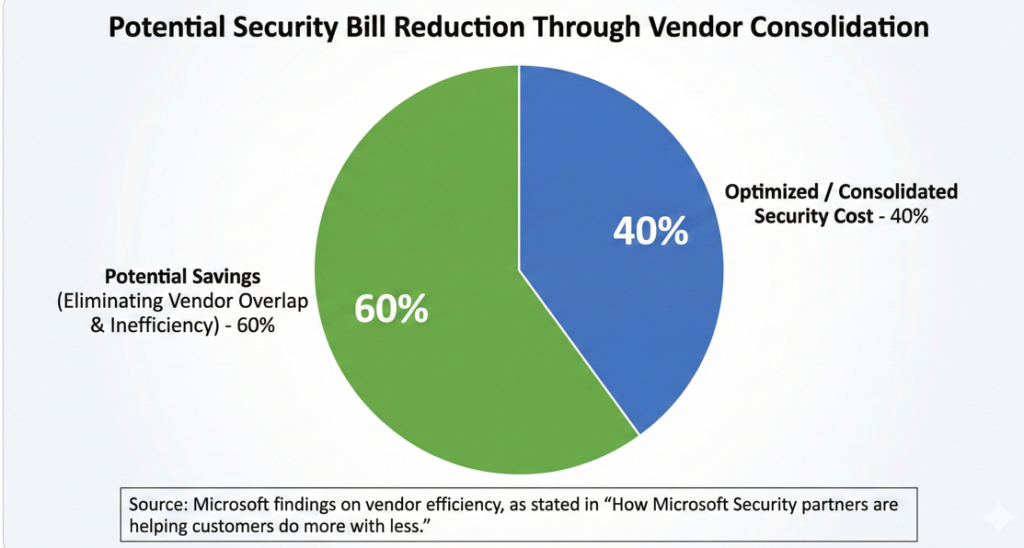
For the CFO, the takeaway is clear: complexity is a cost driver. A consolidated security architecture reduces the Total Cost of Ownership (TCO) while improving incident response speed. It is one of the few areas in enterprise IT where cutting the number of line items can actually improve performance.
The Hidden Liability on the Balance Sheet
While tool sprawl represents a visible waste of budget, a far more dangerous financial risk is lurking in the background: “Shadow Data.” This refers to the unmanaged, untracked data that employees create and store outside of sanctioned corporate systems.
In the rush to adopt new technologies, employees often bypass IT protocols. They might upload customer lists to a personal cloud drive to work from home, or paste sensitive financial projections into a public generative AI tool to draft a summary. This creates a vast, invisible library of corporate assets that the security team cannot see, and therefore cannot protect.
We detailed the forensic implications of this in our article on Shadow Data and Silent Failures: Why Your Cloud Strategy Needs a Forensic Upgrade.3 From a financial perspective, shadow data is an off-balance-sheet liability. It represents a potential regulatory fine (GDPR, CCPA) or a lawsuit waiting to happen.
The scale of this issue is often underestimated by leadership. The Microsoft 2024 Work Trend Index Annual Report4 reveals that 75% of global knowledge workers now use generative AI, yet a staggering portion of this adoption is happening in the shadows. The report highlights that 78% of these users are bringing their own AI tools to work (BYOAI), creating a cycle of unmanaged usage where employees secretly rely on consumer-grade apps to keep up with the pace of business.
If your organization is paying for a top-tier data protection platform but your employees are conducting business on unmonitored “shadow” apps, your ROI on that security investment is effectively zero. The data has already left the building.
The “Fraud Tax” of the AI Era
Efficiency is not just about optimizing what you spend; it is about preventing what you lose. The rise of generative AI has introduced a new form of financial hemorrhage: deepfake-enabled fraud.
Criminals are no longer just hacking databases; they are hacking trust. They use AI to clone the voices of executives or create synthetic video avatars to authorize fraudulent wire transfers. As discussed in Deepfakes in the Enterprise: The New Era of CEO Fraud,5 these attacks are designed to bypass traditional cybersecurity controls by exploiting human psychology and organizational hierarchy.
The financial impact of this threat vector is escalating rapidly. The Internet Crime Report, 2024,6 by the Federal Bureau of Investigation’s Internet Crime Complaint Center (IC3), reveals that reported cybercrime losses in the United States surged to a record $16.6 billion in 2024. This figure represents a “staggering” escalation in financial damage, increasingly driven by AI-enabled tactics such as deepfakes and sophisticated, automated phishing schemes. This figure represents a massive “fraud tax” on the economy. For a single enterprise, a successful deepfake attack can result in the loss of millions of dollars in seconds; losses that are often unrecoverable and uninsured.
For the CFO, this changes the calculus of security investment. Anti-fraud measures are no longer just about compliance; they are about capital preservation. Investing in forensic readiness, technologies that can verify the authenticity of digital communications, is now a critical component of financial risk management.
Strategic Recommendations for the Finance-IT Partnership
To achieve cyber-efficiency, CFOs and CISOs must align on a strategy that prioritizes integration over accumulation.
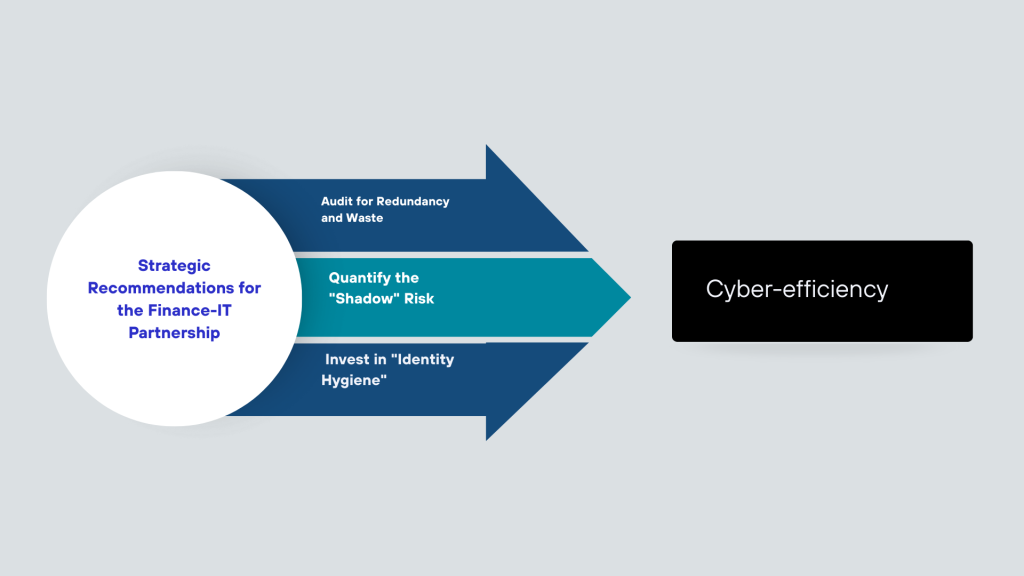
1. Audit for Redundancy and Waste
Initiate a joint audit of the security software stack. Identify tools that have overlapping capabilities. If you have three different tools for endpoint protection, cloud monitoring, and identity verification, ask if a platform approach could deliver the same outcome for 20% less cost. Reduce the “tool sprawl” to free up budget for more advanced forensic capabilities.
2. Quantify the “Shadow” Risk
Require IT to report not just on known assets, but on the discovery of unknown ones. Use tools that map “shadow IT” usage and assign a risk value to it. If 30% of your cloud spend is happening outside of central IT procurement (a common metric cited by analysts), that is 30% of your budget that is actively introducing risk rather than reducing it.
3. Invest in “Identity Hygiene.”
Recognize that in an era of deepfakes, identity verification is a financial control. Funding projects that implement cryptographic signing for internal communications or biometric verification for high-value transactions is not an “IT expense.” It is a control against wire fraud.
Conclusion
The era of writing blank checks for cybersecurity is over. But so is the era of viewing security solely as a cost center. In 2025, a streamlined, forensically ready security posture is a competitive advantage. It reduces the operational drag of tool sprawl, eliminates the hidden liabilities of shadow data, and insulates the company from the catastrophic losses of AI fraud.
By cutting the complexity, you don’t just cut the cost. You clarify the view. And in the world of cyber defense, visibility is the only currency that matters.
Stop paying the “complexity tax.”
Emutare bridges the gap between finance and security by replacing tool sprawl with strategic visibility. Our Cybersecurity Governance and Consultation services streamline your architecture, reducing costs while enhancing defense. We uncover hidden liabilities through rigorous IT Auditing and Asset Management, effectively mitigating “Shadow IT” risks. Furthermore, our AI Adoption Consultation prepares your organization to defend against emerging deepfake fraud. Partner with Emutare to cut costs without cutting safety, achieving true cyber-efficiency.
References
- Emutare. (2025). The “Tool Sprawl” Trap: Why More Security Tools Can Mean Less Security. https://insights.emutare.com/the-tool-sprawl-trap-why-more-security-tools-can-mean-less-security/ ↩︎
- Jakka V. (2022). How Microsoft Security partners are helping customers do more with less. Microsoft. https://www.microsoft.com/en-us/security/blog/2022/07/19/how-microsoft-security-partners-are-helping-customers-do-more-with-less/ ↩︎
- Emutare. (2025). Shadow Data and Silent Failures: Why Your Cloud Strategy Needs a Forensic Upgrade. https://insights.emutare.com/shadow-data-and-silent-failures-why-your-cloud-strategy-needs-a-forensic-upgrade/ ↩︎
- Microsoft. (2024). 2024 Work Trend Index Annual Report. https://www.microsoft.com/en-us/worklab/work-trend-index/ai-at-work-is-here-now-comes-the-hard-part ↩︎
- Emutare. (2025). Deepfakes in the Enterprise: The New Era of CEO Fraud. https://insights.emutare.com/deepfakes-in-the-enterprise-the-new-era-of-ceo-fraud/ ↩︎
- Federal Bureau Of Investigation. (2024). Internet Crime Report, 2024. https://www.ic3.gov/AnnualReport/Reports/2024_IC3Report.pdf ↩︎
Related Blog Posts
- DevSecOps for Cloud: Integrating Security into CI/CD
- Customer Identity and Access Management (CIAM): The Competitive Edge for Australian Businesses
- Infrastructure as Code Security Testing: Securing the Foundation of Modern IT
- Measuring DevSecOps Success: Metrics and KPIs
- Secure CI/CD Pipelines: Design and Implementation
- Certificate-Based Authentication for Users and Devices: A Comprehensive Security Strategy
- IoT Security Challenges in Enterprise Environments

