For the last decade, the metric for success in many security teams was simple: “Patch everything, everywhere, all at once.” The goal was a clean scan report, a sea of green checkmarks indicating that every server, laptop, and cloud instance was updated to the latest version.
In 2026, this goal is not just unrealistic; it is dangerous.
The sheer volume of software vulnerabilities has exploded. Analysis of data from the National Vulnerability Database (NVD)1 reveals that the number of reported Common Vulnerabilities and Exposures (CVEs) reached record levels in 2025, averaging approximately 132 new CVEs per day, and the total number of CVEs published represents roughly a mid-teens percentage increase over 2024 levels. Trying to patch every single one of these flaws is a mathematical impossibility for most IT teams. It results in “patch fatigue,” operational downtime, and, crucially, a false sense of security.
While your team is busy burning the midnight oil to patch a “Critical” severity vulnerability on a print server that sits behind a firewall, they are likely missing a “Medium” severity vulnerability on an internet-facing VPN gateway that attackers are actively exploiting.
The industry has reached a tipping point. We must move from the reactive hamster wheel of “Vulnerability Management” to the proactive, strategic discipline of Continuous Threat Exposure Management (CTEM).
1. The Math of Insecurity: Why “Patch All” Fails
To understand why the old model is broken, we have to look at the numbers. They reveal a stark reality: most vulnerabilities simply do not matter.
According to official data from the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the National Institute of Standards and Technology (NIST), the vast majority of published vulnerabilities are never actively weaponized by attackers. By comparing the 240,000+ total records in the National Vulnerability Database2 against the roughly 1,200 confirmed threats in the CISA KEV catalog, the data reveals that less than 1% of all published CVEs have been exploited in the wild. This distinction allows organizations to focus their limited resources on the small fraction of flaws that pose a confirmed operational risk. The vast majority are theoretical flaws that require such specific conditions to trigger that attackers simply ignore them.
However, the ones they do use, they use fast. Data from VulnCheck’s 2025 Q1 Trends in Vulnerability Exploitation3 reveals that 28.3% of exploited vulnerabilities are weaponized within 24 hours of disclosure.
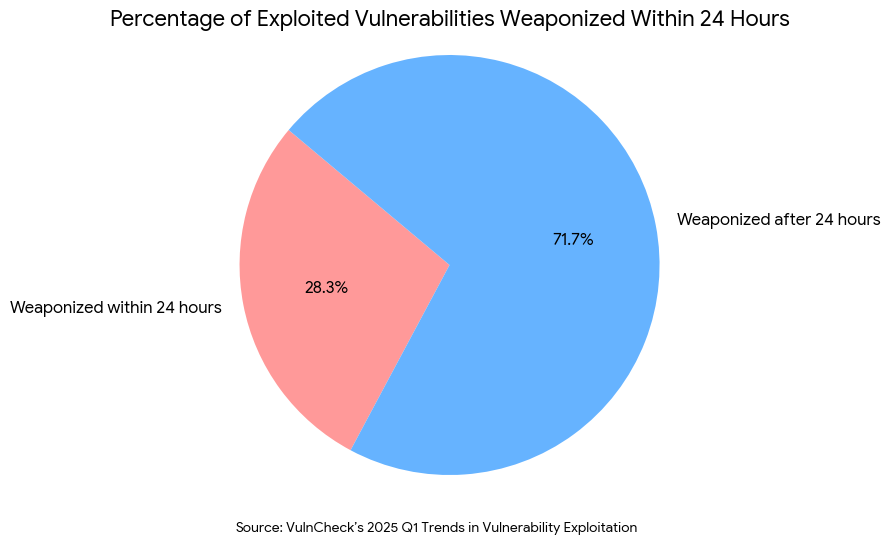
This creates a “Speed vs. Noise” paradox.
- The Noise: You have 10,000 vulnerabilities in your backlog.
- The Speed: You have less than 24 hours to fix the 50 that actually matter.
If you treat every vulnerability as a priority, you have no priorities. The CTEM framework, championed by Gartner, solves this by flipping the script. Instead of asking “Is this system vulnerable?”, it asks “Is this asset exposed and is the threat real?”
2. Defining CTEM: A Cycle, Not a List
CTEM is not a tool; it is a methodology. Unlike traditional vulnerability management, which is often a linear process (Scan -> Ticket -> Patch), CTEM is a continuous cycle designed to align technical security with business risk.
It consists of five distinct phases:
Phase 1: Scoping
You cannot defend the entire internet. Scoping defines what matters right now. This might be “PCI-DSS critical assets” for a retailer or “R&D intellectual property” for a manufacturer.
- The Shift: Moving from “scan everything” to “scan what drives revenue.”
Phase 2: Discovery
This goes beyond the standard vulnerability scanner. It includes the “Shadow IT” and SaaS applications that your scanner misses.
- Internal Insight: As we detailed in SaaS Security Posture Management for Critical Business Applications,4 true discovery must include the API connections and third-party integrations that often serve as backdoors for attackers.
Phase 3: Prioritization
This is the heart of CTEM. It combines Asset Value (how bad is it if this breaks?) with Exploitability (is anyone actually attacking this?). We will discuss this in detail in the next section.
Phase 4: Validation
Don’t just assume a vulnerability is dangerous; prove it. This involves using Breach and Attack Simulation (BAS) tools or automated penetration testing to see if the attack is actually feasible in your specific environment.
- Internal Insight: Validation often requires speed and collaboration. As discussed in ChatOps for Security Teams: Enhancing Collaboration,5 bringing the validation results directly into a chat timeline allows engineers to debate and verify the risk in real-time.
Phase 5: Mobilization
The goal is remediation, but it doesn’t always mean patching. It could mean changing a firewall rule, disabling a service, or accepting the risk. Mobilization ensures the right people take the right action.
3. The New Prioritization: Asset Value vs. Exploitability
If you stop patching everything, what do you patch? The answer lies in a risk matrix that balances two specific variables.
Variable A: Threat Intelligence (The “Likelihood”)
You must rely on authoritative sources to tell you what is being used by adversaries. The gold standard here is the CISA Known Exploited Vulnerabilities (KEV) Catalog.11 If a CVE is on this list, it is not theoretical; it is happening.
- Strategic Link: This is where your investment in intelligence pays off. As we outlined in Measuring ROI of Threat Intelligence Programs,6 a high-quality threat intel feed will tell you not just that a vulnerability is bad, but who is using it (e.g., ransomware gangs vs. state-sponsored spies).
Variable B: Asset Criticality (The “Impact”)
A vulnerability on the CEO’s laptop is different from the same vulnerability on a cafeteria display screen. CTEM demands that you tag your assets based on business value.
The CTEM Prioritization Matrix
| High Exploitability (In CISA KEV / High EPSS) | Low Exploitability (Theoretical Risk) | |
| High Asset Value (Core Database, Payment Gateway) | CRITICAL: Mobilize immediate war room. Patch within 24 hours. | MONITOR: Track for changes in threat landscape. Patch during standard cycle. |
| Low Asset Value (Guest Wi-Fi, Test Server) | CONTAIN: Isolate the asset or apply mitigating controls. Patch when able. | IGNORE: Accept the risk. Do not waste resources here. |
By applying this matrix, you might find that you can safely ignore 80% of your backlog, allowing you to focus laser-like intensity on the 20% that could cause a breach.
4. The “Mobilization” Challenge: Fixing the Process
The hardest part of CTEM is not technical; it is organizational. “Mobilization” implies movement, yet many organizations are stuck in friction.
Verizon’s2025 Data Breach Investigations Report7 (DBIR) highlights that 20% of breaches now involve the exploitation of vulnerabilities as an initial access step, a 34% increase from the previous year. The attackers are moving faster than our internal ticketing systems.
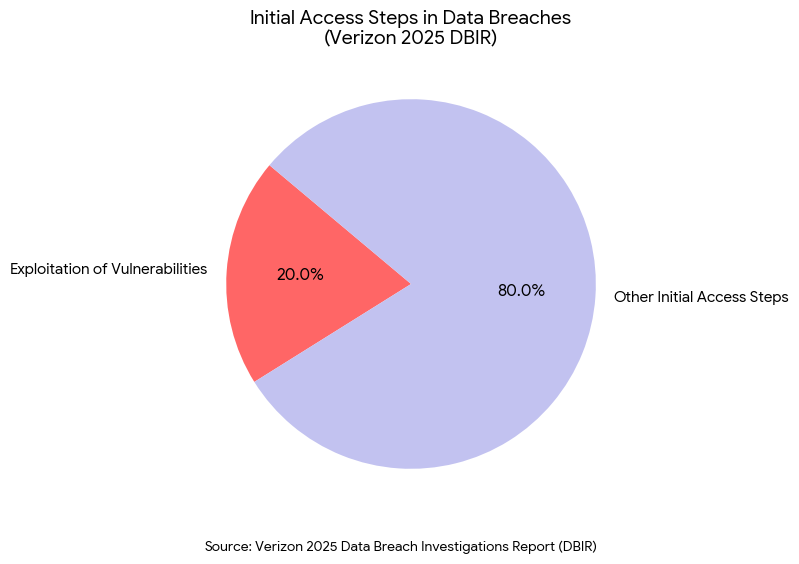
To fix this, we must democratize the remediation process.
- Stop throwing PDFs over the fence. Sending a 200-page vulnerability report to a DevOps lead is a recipe for inaction.
- Start using ChatOps. Push the specific, prioritized alert to the specific channel of the team that owns the asset. “Team, Server X has a CISA-listed vulnerability. Here is the context. Can we patch or isolate by 2:00 PM?”
This approach reduces the “Mean Time to Remediate” (MTTR) by removing the administrative overhead of logging into multiple portals to understand the risk.
Conclusion
The transition to Continuous Threat Exposure Management is an acknowledgment of reality. We cannot secure everything equally. We cannot patch faster than the internet produces code.
By adopting CTEM, we shift our focus from “compliance” (did we patch the list?) to “resilience” (did we reduce the exposure?). We stop wasting expensive engineering hours on theoretical bugs and start deploying our resources against the threats that are actively knocking on our digital doors.
In 2026, the safest organization is not the one with the empty patch queue. It is the one that knows exactly which exposures define its risk, and attacks them with precision.
Stop drowning in patch requests and start managing actual risk.
Emutare empowers your transition to Continuous Threat Exposure Management with precision-driven IT and IoT Vulnerability Management. We help you cut through the noise by identifying critical assets through comprehensive Cybersecurity Risk Assessments and deploying advanced SIEM and XDR solutions for real-time threat detection. With our strategic Cybersecurity Advisory and optimized Patch Management services, you can ensure your team focuses only on the exposures that truly threaten your business. Build a resilient, intelligence-led defense today with Emutare
References
- National Institute of Standards and Technology. (2026). National Vulnerability Database. U.S. Department of Commerce. Retrieved January 14, 2026, from https://nvd.nist.gov/general/nvd-dashboard ↩︎
- National Institute of Standards and Technology. (2026). National Vulnerability Database. U.S. Department of Commerce. Retrieved January 14, 2026, from https://nvd.nist.gov/general/nvd-dashboard ↩︎
- VulnCheck (2025). 2025 Q1 Trends in Vulnerability Exploitation. https://www.vulncheck.com/blog/exploitation-trends-q1-2025 ↩︎
- Emutare. (2025). SaaS Security Posture Management for Critical Business Applications. https://insights.emutare.com/saas-security-posture-management-for-critical-business-applications/ ↩︎
- Emutare. (2025). ChatOps for Security Teams: Enhancing Collaboration. https://insights.emutare.com/chatops-for-security-teams-enhancing-collaboration/ ↩︎
- Emutare. (2025). Measuring ROI of Threat Intelligence Programs: A Strategic Framework for Australian Organizations. https://insights.emutare.com/measuring-roi-of-threat-intelligence-programs-a-strategic-framework-for-australian-organizations/ ↩︎
- Verizon. (2025). 2025 Data Breach Investigations Report. https://www.verizon.com/business/resources/Tbb1/reports/2025-dbir-data-breach-investigations-report.pdf ↩︎
Related Blog Posts
- Cybersecurity Essentials for Startups: Safeguarding Your Business from Digital Threats
- Insider Threats: Detection and Prevention Strategies
- Securing Microsoft 365 Email Environments: A Comprehensive Guide
- Crisis Communication During Security Incidents: A Strategic Approach
- Building a Security Operations Center (SOC): Key Components
- Implementing Single Sign-On: Pros, Cons, and Best Practices
- Backup and Recovery: Building Resilience Against Ransomware

