In the digital economy, data travels at the speed of light, but the laws governing that data stop abruptly at physical borders. This is the central paradox of modern cybersecurity. We live in a world where a security operations center in New York might need to investigate a compromised server in Frankfurt, which contains customer records from Brazil. The investigation itself is necessary to stop the threat, yet the act of investigating, specifically, moving or accessing that data across jurisdictional lines, can be a violation of the very laws you are trying to uphold.
For business leaders and IT professionals, this “sovereignty struggle” is no longer just a legal headache; it is an operational crisis. How do you respond to a global cyber incident when data privacy laws like the GDPR in Europe, the LGPD in Brazil, or the PIPL in China demand that data remain local?
The traditional “grab and go” approach to digital forensics, where security teams image a drive and upload it to a central cloud for analysis, is dead. It has been killed by a complex web of data localization laws and sovereignty requirements. To survive in this new landscape, organizations must adopt a strategy that fuses legal awareness with technical agility. We must move away from the idea of “borderless” data and embrace a new model: Privacy-Preserving Forensics.
The Invisible Risk: Shadow Data and Jurisdictional Ambiguity
The first hurdle in any cross-border investigation is often the most embarrassing one: organizations do not actually know where their data lives. In the era of multi-cloud architectures and remote work, data has a habit of drifting. It replicates into backups, gets copied into development environments, or lingers in “temporary” storage buckets that were never deleted.
This creates a massive liability during an investigation. If you do not have a clear map of your data estate, you might inadvertently pull sensitive French citizen data onto a US server, triggering a GDPR violation before you have even identified the malware. As previously covered, this phenomenon is often referred to as “Shadow Data,” and it represents a silent failure in cloud strategy.1 To learn more about the risks of unmonitored data assets, read Shadow Data and Silent Failures: Why Your Cloud Strategy Needs a Forensic Upgrade1 here.
When Shadow Data exists across borders, it creates “Jurisdictional Ambiguity.” A forensic analyst might believe they are investigating a log file hosted in a benign jurisdiction, only to find that the underlying data subjects are protected by a sovereignty mandate they were unaware of. The solution begins with visibility, but it ends with a fundamental shift in how we handle the evidence itself.
The Conflict: The Duty to Investigate vs. The Duty to Protect
There is a natural tension between security and privacy. Security teams want maximum context (full packet captures, unredacted logs, user names) to attribute an attack and understand its scope. Privacy regulators, conversely, want minimum exposure (data minimization, purpose limitation, localized processing).2
This tension snaps tight during a cross-border incident. The European Data Protection Board (EDPB) recommendations on supplementary measures2 has made it clear that transferring personal data to third countries (like the US) for administrative purposes requires strict supplementary measures. According to their guidelines on data transfers, mere contractual clauses are often insufficient if the data can be accessed by foreign authorities.
This puts the CISO in a bind. If you leave the data in the local jurisdiction, your central incident response team cannot see it to stop the breach. If you move the data to your central team, you break the law.
The only way to navigate this minefield is to stop treating “investigation” as a reactive scramble and start treating it as a pre-planned capability. This is the core concept of Forensic Readiness. It is not enough to have tools; you must have a “ready” state where the legal pathways for data transfer are established before the crisis hits. For a deeper dive into establishing these protocols, see Forensic Readiness: Preparation for Investigations3
Readiness in a cross-border context means pre-deploying forensic agents that can process data locally and only transmit the metadata or sanitized insights needed for the investigation.
The Bridge: Anonymization as a Forensic Enabler
So, how do we practically investigate a breach in a strict jurisdiction without moving sensitive personal data? The answer lies in transforming the data so that it is no longer “personal” but remains “forensically valuable.”
This brings us to the critical distinction between Anonymization and Pseudonymization. In many legal frameworks, if data is truly anonymized, it falls outside the scope of privacy regulations (like GDPR), allowing it to move freely across borders.3 However, for a forensic investigator, true anonymization can be destructive; if you scrub all user identifiers, you might lose the ability to track the attacker’s lateral movement.
The sweet spot for cross-border forensics is often Pseudonymization. This technique replaces private identifiers (like names or IP addresses) with artificial identifiers (pseudonyms). The data can then be transferred and analyzed centrally to find patterns of attack. If a specific threat is identified that requires knowing the real user’s identity, a “re-identification” process can be triggered locally, under strict legal supervision.
Implementing these techniques correctly is nuanced. We have detailed the technical differences and implementation strategies in Anonymization vs. Pseudonymization Techniques: A Comprehensive Guide for Modern Data Protection.4 By using these techniques, organizations can effectively decouple the security signal from the personal data, allowing the investigation to proceed globally while the risk remains contained locally.
Research from the National Institute of Standards and Technology (NIST) Guide to Integrating Forensic Techniques into Incident Response5 supports this approach. In their guidelines on integrating forensic techniques, they emphasize that data handling must minimize the exposure of sensitive information while preserving the integrity of the evidence.
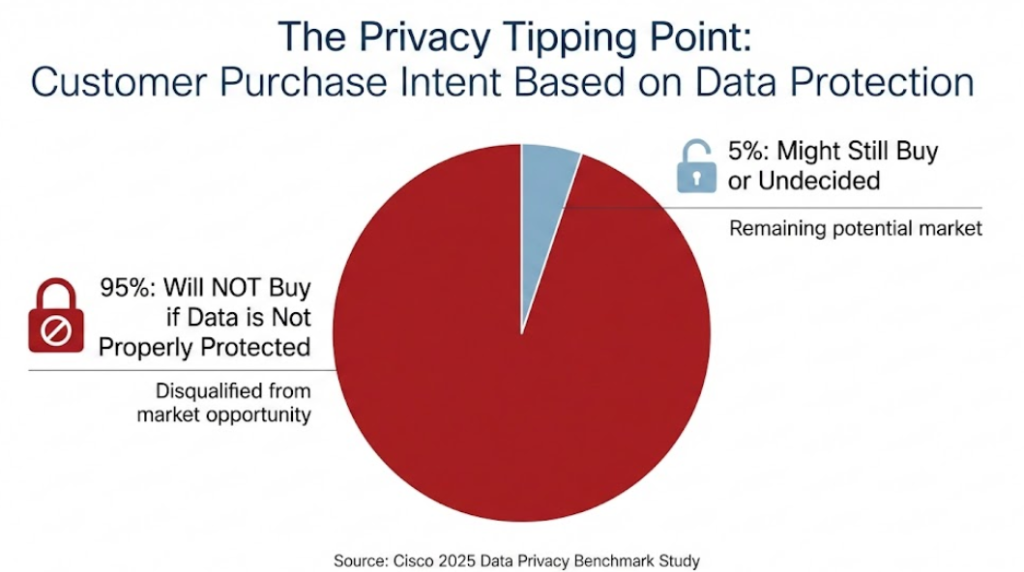
The Cisco 2025 Data Privacy Benchmark Study6 identifies a critical tipping point in commercial trust. It reveals that 95% of customers explicitly state they will not buy from an organization if their data is not properly protected. This data confirms that privacy mechanisms like pseudonymization are no longer just ‘security’ controls; they are a prerequisite for revenue. Failing to implement them effectively disqualifies a company from 95% of its potential market opportunities.
Practical Implementation: A Cross-Border Forensic Playbook
To move from theory to practice, organizations need a specific playbook for cross-border incidents. This is not just an IT policy; it is a governance framework that involves Legal, HR, and Security.
Here is a structured approach to building a sovereignty-compliant investigation capability.
1. The “In-Country” Triage Model
Instead of defaulting to a “centralized data lake” where all logs are shipped to headquarters, adopt a federated approach. Deploy forensic collectors in each jurisdiction (e.g., within your EU Virtual Private Cloud).
- Action: configure these collectors to perform “local triage.” They should scan for Indicators of Compromise (IoCs) like file hashes or malware signatures locally.
- Result: You only transfer the alert (“We found Malware X”), not the entire drive image containing customer data.
2. Static vs. Dynamic Pseudonymization
Implement dynamic pseudonymization at the log ingestion point. When logs are generated in a strict jurisdiction (e.g., Germany), the logging system should automatically hash user IDs before they leave the region.
- The Key: The “re-identification key” must stay in Germany. The central SOC in the US sees “User_12345 accessed Malicious_File.” They can determine this is a security incident without knowing who User_12345 is.
- Escalation: If it turns out “User_12345” is a compromised admin account, the US team issues a formal request to the German legal entity to unlock the identity for remediation, ensuring the process follows local labor laws.
3. “Compute-to-Data” Architectures
For heavy forensic analysis (like processing terabytes of email archives), do not move the data to the tool; move the tool to the data.
- Strategy: Spin up temporary, ephemeral forensic workstations inside the jurisdiction where the data resides. Remote analysts can access these workstations via secure, audited gateways (like VDI), but copy/paste and file transfer capabilities are disabled.
- Benefit: The data never legally “leaves” the country, even if a remote analyst is viewing it.
This aligns with principles from The Sedona Conference,7 a leading research institute for law and policy. Their “International Principles on Discovery, Disclosure, and Data Protection” highlight the importance of processing data within its home jurisdiction whenever possible to mitigate conflicts of law.
4. Automated Data Expiration (Defensible Deletion)
One of the biggest risks in cross-border investigations is “over-collection.” Investigators often grab everything “just in case.” In a sovereignty context, this is dangerous.
- Policy: Implement strict retention policies for forensic artifacts. If you collected a memory dump from a French server, it should be automatically purged after the investigation closes.
- Tech: Use forensic platforms that support “time-bombing” data — automatically deleting copies after a set period unless a legal hold is renewed.

The Role of Documentation and Transparency
Regulators are generally reasonable if they see a “good faith” effort to comply. The worst thing you can do is hide the fact that you accessed cross-border data.
Every step of the cross-border investigation must be documented. This is part of the Forensic Readiness mandate. You need an audit trail that shows:
- Why the data was accessed (The Security Necessity).
- What techniques were used to minimize privacy impact (e.g., Pseudonymization).
- Who accessed it and from where.
This documentation is your “Get Out of Jail Free” card. If a regulator questions why a US analyst looked at European server logs, you can present the audit trail showing that the analyst only viewed pseudonymized metadata until a confirmed threat was identified.
Conclusion: Sovereignty as a Design Constraint, Not a Blocker
The era of unrestricted global data movement is over. We are entering a phase of the internet that is bordered, regulated, and partitioned. For security leaders, this can feel like a step backward. It feels like friction.
However, if we reframe the problem, we see that “sovereignty” is simply a design constraint. Just as we design systems for latency or throughput, we must now design them for privacy and jurisdiction.
The combination of Forensic Readiness (being prepared), Pseudonymization (protecting identity), and robust Shadow Data discovery (knowing your terrain) creates a resilient architecture. It allows us to hunt threats globally without trampling on local rights.
By adopting these privacy-preserving forensic techniques, we do more than just avoid fines. We build trust. We demonstrate to our customers and employees that we can protect their security without compromising their privacy. In 2025, that balance is not just a nice-to-have; it is the definition of a mature digital enterprise.
Don’t let jurisdictional borders stall your defense. Emutare empowers your organization to balance global security with local privacy through expert Cybersecurity Governance and Advisory services. We help you build the “Forensic Readiness” essential for modern investigations, from robust Incident Response Planning to the implementation of compliant Data Protection Controls. Whether navigating complex regulations or deploying SIEM/XDR for safe visibility, we bridge the gap between legal mandates and technical agility
References
- Emutare. (2025). Shadow Data and Silent Failures: Why Your Cloud Strategy Needs a Forensic Upgrade. https://insights.emutare.com/shadow-data-and-silent-failures-why-your-cloud-strategy-needs-a-forensic-upgrade/ ↩︎
- European Data Protection Board (EDPB). (2021). Recommendations 01/2020 On Measures That Supplement Transfer Tools To Ensure Compliance With The Eu Level Of Protection Of Personal Data. https://www.edpb.europa.eu/our-work-tools/our-documents/recommendations/recommendations-012020-measures-supplement-transfer_en ↩︎
- Emutare. (2025). Forensic Readiness: Preparation for Investigations. https://insights.emutare.com/forensic-readiness-preparation-for-investigations/ ↩︎
- Emutare. (2025). Anonymization vs. Pseudonymization Techniques: A Comprehensive Guide for Modern Data Protection. https://insights.emutare.com/anonymization-vs-pseudonymization-techniques-a-comprehensive-guide-for-modern-data-protection/ ↩︎
- National Institute of Standards and Technology (NIST). (2006). Guide to Integrating Forensic Techniques into Incident Response. https://csrc.nist.gov/pubs/sp/800/86/final ↩︎
- Cisco. (2025). Cisco 2025 Data Privacy Benchmark Study. https://www.cisco.com/c/en/us/about/trust-center/data-privacy-benchmark-study.html ↩︎
- The Sedona Conference Working Group Series. (2017). International Principles on Discovery, Disclosure & Data Protection in Civil Litigation (Transitional Edition. The Sedona Conference Working Group. https://www.thesedonaconference.org/sites/default/files/publications/International%2520Litigation%2520Principles_Transitional%2520Ed_Jan%25202017.pdf ↩︎
Related Blog Posts
- Board Reporting on Cybersecurity: What Executives Need to Know
- Multi-Factor Authentication: Comparing Different Methods
- Secrets Management in DevOps Environments: Securing the Modern Software Development Lifecycle
- Zero Trust for Remote Work: Practical Implementation
- DevSecOps for Cloud: Integrating Security into CI/CD
- Customer Identity and Access Management (CIAM): The Competitive Edge for Australian Businesses
- Infrastructure as Code Security Testing: Securing the Foundation of Modern IT
- Measuring DevSecOps Success: Metrics and KPIs

