It is the nightmare scenario every CISO dreads, and it usually happens at 3:00 AM on a Saturday.
A security analyst notices anomalous traffic on a primary database server. Files are being encrypted at a rate of 10,000 per minute. It is unmistakably ransomware. The containment algorithms have failed. The malware is moving laterally, seeking the backup servers and the cloud repositories.
At this moment, the organization faces the most agonizing decision in modern business: Do we activate the “Kill Switch”?
Pulling the plug, severing the organization’s connection to the internet, and internally isolating networks, stops the bleeding. It halts the exfiltration of sensitive data and prevents the malware from contacting its command-and-control (C2) servers. But it also stops the heart of the business. Orders cannot be processed. Hospitals cannot access patient records. Factories grind to a halt. The financial damage of the “cure” can sometimes exceed the cost of the disease.
For years, this decision has been treated as a tactical IT call. But in 2026, with the speed of automated attacks and the complexity of hybrid cloud environments, the “Kill Switch” is a strategic business decision that must be architected long before the crisis begins.
The Velocity of Destruction
The debate over disconnection is driven by one factor: speed.
Legacy ransomware took days to proliferate. Modern “ransomware-as-a-service” (RaaS) kits are designed for speed. A 2025 analysis by Google Mandiant on “M-Trends“1 reveals that the median dwell time for ransomware incidents involving victim notification has stabilized at 5 days, while the global median dwell time for all intrusion types stands at 11 days.
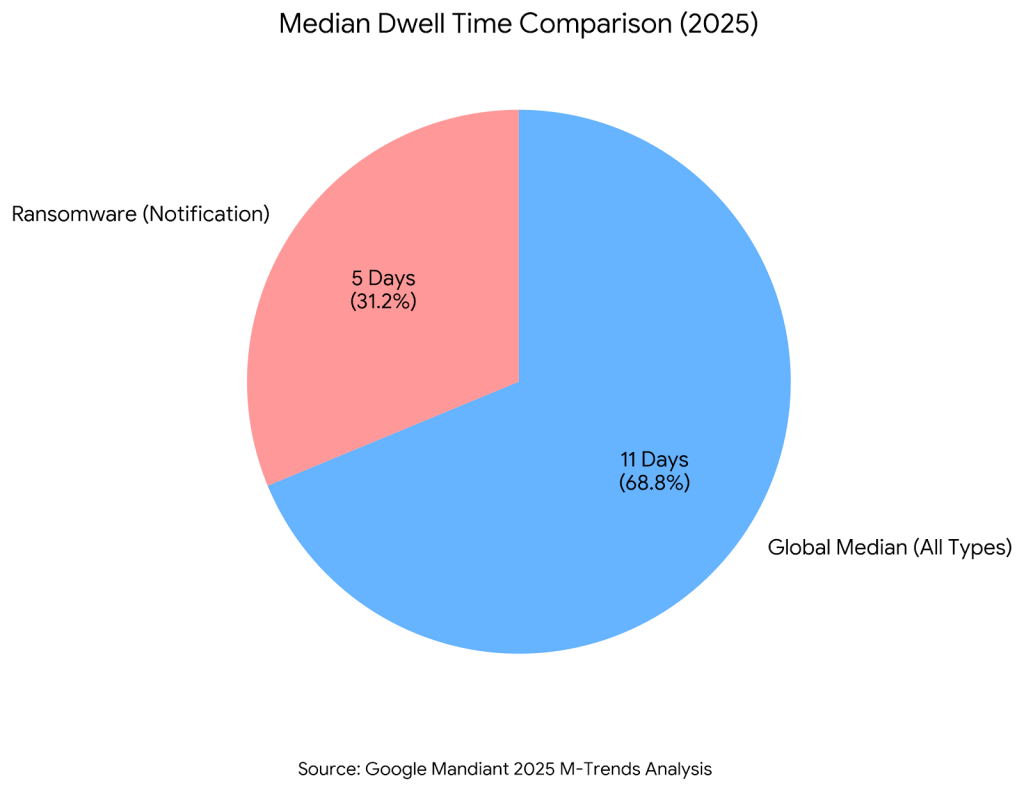
This velocity renders the traditional “wait and see” approach obsolete. By the time a committee convenes to discuss the legal implications of shutting down the customer portal, the data is already gone.
However, the decision to disconnect is rarely binary. In a modern, interconnected ecosystem, “pulling the plug” is not as simple as yanking a network cable. When your infrastructure is defined by code and spread across three different cloud providers, what does “disconnection” even look like?
This is where the maturity of your Integration of Vulnerability Management with DevOps2 becomes the deciding factor. Organizations that have integrated security into their DevOps pipelines have a distinct advantage: resilience. If your infrastructure is immutable (meaning servers are replaced rather than patched) and you can redeploy your entire environment from code in hours, you can afford to be aggressive with the Kill Switch. You can “burn down” the infected segment and rebuild it fresh. Organizations without this capability, those relying on manual configurations and fragile legacy servers, hesitate. They know that if they turn it off, they might not be able to turn it back on.
The Economics of Silence
The hesitation to disconnect is driven by the terrifying cost of downtime.
For an e-commerce giant, an hour of downtime can cost millions. For a healthcare provider, it risks patient safety. But this cost must be weighed against the catastrophic cost of a data breach.
Regulatory bodies are changing this calculus. Under strict regimes like GDPR and the new SEC disclosure rules, the loss of customer PII (Personally Identifiable Information) carries massive fines and reputational ruin. If disconnecting the internet saves the data but kills the revenue for a day, the math often favors disconnection. The SEC Public Company Cybersecurity Disclosures; Final Rules3 mandate disclosing material cyber incidents within four business days, removing the option to quietly manage a breach. This forces a public choice between a controlled outage and an uncontrolled leak. A voluntary shutdown signals proactive governance to shareholders, whereas staying online and losing data signals negligence. In the eyes of the market, a temporary revenue pause is a manageable cost; a governance failure is not.
This is fundamentally a privacy issue. As outlined in the Privacy by Design: Implementation Framework for Modern Organizations,4 a robust privacy architecture includes “Privacy by Default.” In the context of a cyberattack, the default state should favor the protection of data over the availability of services. A Privacy by Design framework encourages network segmentation—creating airtight compartments within the network. This allows an organization to use a “Partial Kill Switch,” severing only the infected limb (e.g., the HR system) while keeping the vital organs (e.g., the production line) operational. Without this segmentation, the only option is a total blackout.
The Human Element: Who Has the Authority?
Technology aside, the Kill Switch debate often fails due to human psychology.
Imagine a junior security analyst who spots the intrusion. They know they should isolate the network. But they also know that isolating the network will disrupt the CEO’s presentation and cost the company money. They hesitate. They send an email. They wait for approval.
That delay is fatal.
Empowering the “Human Firewall” is critical. As discussed in Security Awareness Program Design: Beyond Compliance,5 security awareness is not just about teaching users not to click links; it is about empowering them to act when they see something wrong. A mature organization gives specific, pre-authorized personnel the authority to hit the Kill Switch without fear of retribution.
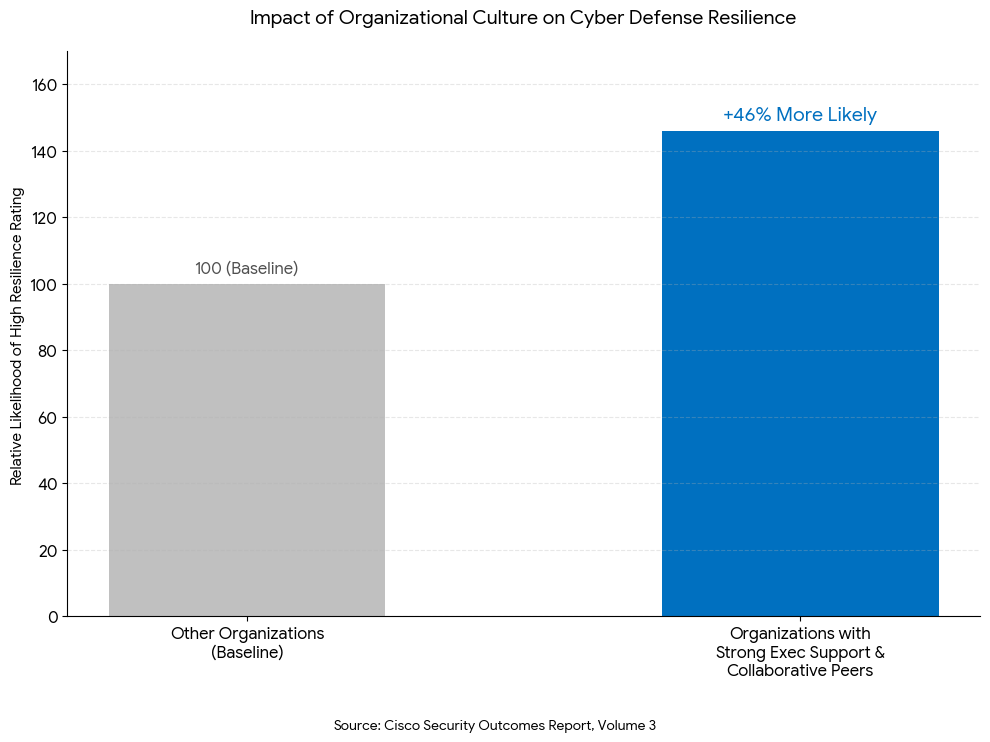
Response times improves by significantly when organizations have a pre-signed “Safe Harbor” policy for employees who authorize emergency shutdowns. When staff know they won’t be fired for a false positive, they act faster to stop the real threats. According to the Cisco Security Outcomes Report, Volume 3,6 organizational culture acts as a decisive factor in cyber defense capabilities. After analyzing data from over 4,700 security professionals globally, the study found that organizations with strong executive support and a collaborative peer environment were 46% more likely to achieve high resilience ratings. This data suggests that when leadership fosters a supportive rather than punitive environment, security teams are significantly better equipped to withstand and recover from critical incidents.
Designing the Kill Switch Protocol
So, how does a modern organization build a functional Kill Switch protocol? It requires a blend of technical engineering and executive governance.
1. Define “Severity 1” Explicitly
You cannot make this decision in the heat of the moment. The C-Suite must agree in advance on the criteria for a total shutdown.
- Example Criteria: “Any confirmed lateral movement toward the Customer Database.”
- Example Criteria: “Detection of ransomware signatures on more than 5 endpoints.”
2. The Technical “Big Red Button”
In a cloud environment, you cannot physically unplug a router. You need a scripted response.
- Scripted Isolation: Engineers should write scripts that, when executed, immediately apply “Deny All” rules to Security Groups or firewalls, effectively quarantining a Virtual Private Cloud (VPC).
- Identity Revocation: A Kill Switch might not cut the network; it might cut access. A “Panic Button” in your Identity Provider (IdP) can instantly revoke all user sessions, forcing every human and bot to re-authenticate. This stops the attacker’s compromised credentials from working.
3. The Communication “Lifeboat”
If you kill the network, you also kill email, Slack, and Teams. How will your incident response team communicate?
- Out-of-Band Comms: You must have a pre-established, separate communication channel (e.g., Signal groups on personal devices, or a dedicated external crisis portal) that is not dependent on the corporate network.
The “False Positive” Fear
The greatest argument against the Kill Switch is the fear of a false positive, shutting down the business for a glitch.
This is a valid concern, but it is a manageable risk. This is where Integration of Vulnerability Management with DevOps plays a vital role again. Continuous monitoring and automated baselining help distinguish between a spike in legitimate traffic (e.g., Black Friday sales) and a spike in malicious traffic (e.g., data exfiltration).4 The more “observable” your stack is, the more confidence you have when you decide to pull the plug.
Furthermore, a “Soft Kill” can be implemented. Instead of severing the connection entirely, traffic can be throttled or redirected to a “waiting room” page. This preserves the user experience while buying the security team time to investigate.
The Legal Aftermath
There is also a risk management dimension to the Kill Switch. If you are a SaaS provider, pulling the plug guarantees a breach of contract, but the newly released NISTSP 800-61 Revision 37 provides the cover to do it. The guide explicitly categorizes “shutting down critical services” as a leadership decision rather than a simple technical failure.
Critically, the new framework mandates that responders weigh the “functional impact” (uptime) against the “data impact” (breach) when prioritizing a response. In court, arguing that you executed a Kill Switch because the risk of data theft outweighed the functional impact is a defensible position backed by federal standards. Arguing that you kept the system running to avoid a service penalty and allowed the data to be stolen is negligence.
Your Privacy by Design: Implementation Framework for Modern Organizations should document this hierarchy of values. If your policy explicitly states that “Data Integrity supersedes System Availability,” you have a legal shield when customers complain about the downtime.
Conclusion
The “Kill Switch” is not a sign of defeat; it is a tool of survival.
In an era where attackers move at the speed of light, the ability to stop the clock is the most powerful weapon a defender has. But this weapon cannot be forged in the middle of a battle. It requires the foresight to build resilient systems, the courage to empower employees, and the wisdom to prioritize long-term trust over short-term uptime.
When the 3:00 AM call comes, the question should not be “Can we afford to shut it down?” The question should be “Why haven’t we done it yet?”
Don’t wait for a crisis to architect your survival. Emutare empowers you to execute the “Kill Switch” with confidence. Our Incident Response and Disaster Recovery Planning ensures your protocols are battle-ready long before the 3:00 AM alarm. We fortify your defenses through Cybersecurity Governance and Vulnerability Management, helping you prioritize data integrity over short-term uptime. Whether empowering staff with Awareness Training or architecting resilient Network Security, Emutare transforms your defensive measures into a strategic business advantage. Prepare your organization today to stop the clock without stopping the business.
References
- Google. (2025). M-Trends 2025 Report. https://services.google.com/fh/files/misc/m-trends-2025-en.pdf ↩︎
- Emutare. (2025). Integration of Vulnerability Management with DevOps. https://insights.emutare.com/integration-of-vulnerability-management-with-devops/ ↩︎
- US Securities and Exchange Commission. (2022). Public Company Cybersecurity Disclosures; Final Rules. https://www.sec.gov/files/33-11216-fact-sheet.pdf ↩︎
- Emutare. (2025). Privacy by Design: Implementation Framework for Modern Organizations. https://insights.emutare.com/privacy-by-design-implementation-framework-for-modern-organizations/ ↩︎
- Emutare. (2025). Security Awareness Program Design: Beyond Compliance. https://insights.emutare.com/security-awareness-program-design-beyond-compliance/ ↩︎
- Cisco. (2025). Security Outcomes Report, Volume 3. https://blogs.cisco.com/security/achieving-security-resilience-findings-from-the-security-outcomes-report-vol-3? ↩︎
- National Institute of Standards and Technology. (2025). SP 800-61 Revision 3. https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-61r3.pdf ↩︎
Related Blog Posts
- GDPR Compliance for Australian Companies with EU Customers: A Comprehensive Guide for 2025
- Developing Cyber Threat Intelligence Requirements: A Strategic Framework for Modern Organizations
- Cybersecurity Insurance for Australian SMBs: A Critical Shield Against Rising Cyber Threats
- Securing Data Pipelines for AI Training: A Comprehensive Guide for Australian Enterprises
- Hash Functions and Their Applications in Security
- PCI DSS: Implementation Guide for Australian Merchants
- Managed Security Services: When to Outsource

