The thrill of a merger or acquisition (M&A) is often found in the synergy of the deal: new markets, new technologies, and new talent. But in 2026, the greatest risk to a successful exit isn’t in the financial ledger; it is in the code repositories, the employee habits, and the silent, unpatched vulnerabilities you inherit the moment the ink dries.
Historically, due diligence focused on balance sheets and legal disputes. Today, that approach is dangerously incomplete. When you acquire a company, you are not just buying their revenue stream; you are acquiring their technical debt, their privacy shortcuts, and their cybersecurity culture. As the cautionary tale of Verizon’s acquisition of Yahoo reminds us, where a $350 million price reduction was negotiated after a massive data breach came to light, cyber risk is financial risk.
Modern M&A requires a new kind of audit. We must move beyond checking boxes and start looking under the digital hood.
The Hidden Liability: “Technical Security Debt”
In the rush to scale, startups and mid-market companies often prioritize speed over security. They push code to production without rigorous testing, delay patches to avoid downtime, and leave legacy APIs running in the background. In the industry, we call this “technical security debt.”
When you acquire a target, you inherit the interest payments on that debt.
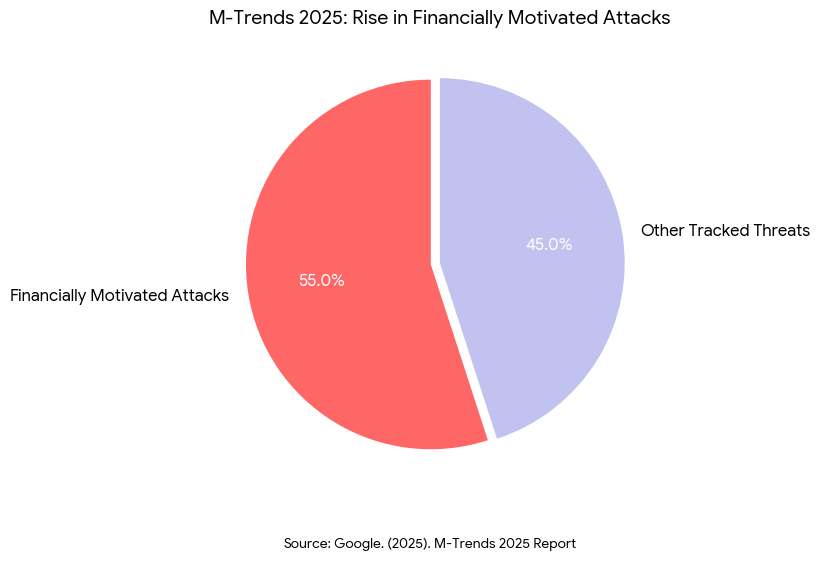
The 2025 M-Trends report1 by Mandiant identifies a significant rise in financially motivated attacks, which now account for 55% of all tracked threats. The research highlights that threat actors actively exploit the security gaps and unsecured data repositories that are often created during complex cloud migrations and organizational changes. This trend confirms that the chaotic transitional period of a deal provides a prime opportunity for attackers to leverage integration vulnerabilities for extortion. This spike isn’t random; it is the direct result of combining two dissimilar IT environments where vulnerabilities can hide in the complexity.
This is why traditional vulnerability scanning isn’t enough during due diligence. You need to understand how the target company builds software. Do they scan for vulnerabilities daily, or only when an auditor asks? Is their patching automated, or does it rely on a spreadsheet?
To truly assess the quality of the asset you are buying, you must look at their development pipeline. A company that has successfully achieved the Integration of Vulnerability Management with DevOps2 is an asset. They have built a system where security is self-healing. Conversely, a company that treats security as a final “gate” before release is a liability. Their code is likely riddled with dormant flaws that will become your emergency the moment you integrate their network with yours.
The Regulatory Time Bomb
If technical debt is a slow-burning fire, privacy violations are a ticking bomb. The regulatory landscape has shifted aggressively, and liabilities are now retroactive. If the company you are acquiring collected user data in 2022 without proper consent, you are buying that lawsuit in 2026.
Consider the Marriott-Starwood acquisition. Marriott inherited a breach that had been festering in Starwood’s systems for years. The result was not just technical cleanup costs, but a massive fine from the UK’s Information Commissioner’s Office (ICO). The lesson? You cannot plead ignorance for the sins of the company you bought.
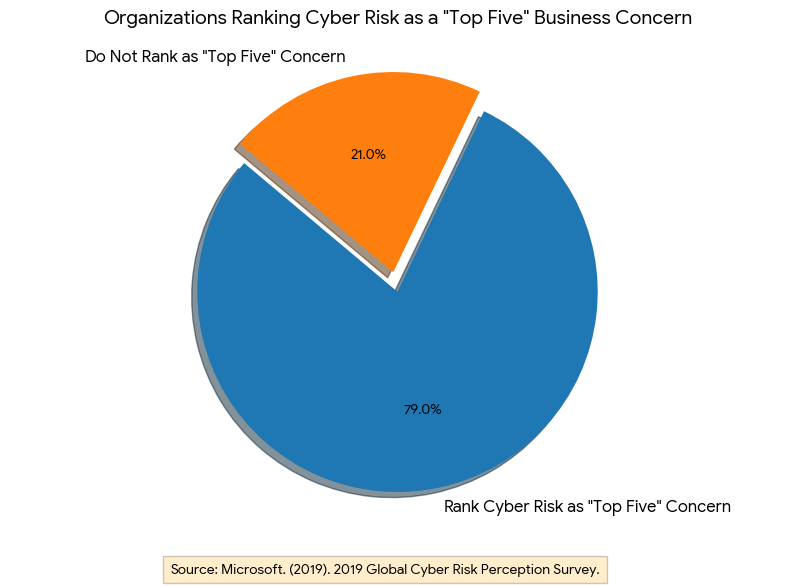
Research conducted by Microsoft3 (in partnership with Marsh) indicates that the sentiment behind the “deal breaker” statistic is driven by anxiety over financial impact. Their survey found that 79% of organizations now rank cyber risk as a “top five” business concern, pushing it into the center of board-level M&A discussions. Yet, many acquirers still fail to ask the hard questions about data lineage. Where does the data live? Who has access to it? Is it minimized?
A target company that has adopted a Privacy by Design: Implementation Framework for Modern Organizations4 offers a significantly higher value proposition. These organizations have architecture that segregates data, enforces consent, and minimizes exposure by default. During due diligence, you must verify if privacy is baked into the architecture or if it is merely a policy document ignored by the engineering team. If it is the latter, you should calculate the potential regulatory fines and deduct them from the deal price.
The “Culture Clash” Vulnerability
Technology is easy to audit; culture is hard. Yet, the human element remains the most volatile variable in any merger. During an acquisition, employees at the target company are often stressed, distracted, and uncertain about their futures. This makes them prime targets for social engineering.
Hackers know this. They monitor financial news wires for M&A announcements and immediately launch targeted phishing campaigns mimicking “HR Benefit Changes” or “IT System Migration” emails. If the company you are buying has a weak security culture, their employees will click those links.
Academic research reinforces this risk. A study on “The Role of Cybersecurity in Mergers and Acquisitions“ 5 emphasizes that cybersecurity is fundamentally a cultural challenge, noting that divergent organizational behaviors often obstruct the implementation of unified protocols and create human-centric vulnerabilities that technical controls cannot mitigate.
This is where you must evaluate the target’s “human firewall.” Do they rely on dry, annual compliance videos that everyone skips? Or have they built a robust culture of defense? A mature organization will have a Security Awareness Program Design: Beyond Compliance6 that focuses on behavior modification rather than just checking a box. If the target company’s employees treat security as “IT’s problem,” you are importing a user base that will actively undermine your own security controls.
A Framework for Cyber Due Diligence
To protect your investment, you need a due diligence framework that mirrors the sophistication of the threat landscape. Here is a practical approach for modern dealmakers:
1. The “Code & Pipeline” Audit
Don’t just scan the network; scan the repositories.
- Ask: Can you show us your vulnerability backlog? (If it’s empty, they aren’t looking).
- Ask: How long does it take you to patch a critical CVE in production? (If the answer is >48 hours, that is a red flag).
- Verify: Look for evidence of automated security testing in their CI/CD pipeline.
2. The Data Lineage Stress Test
Assume the data is “toxic” until proven safe.
- Ask: Can you map the flow of PII (Personally Identifiable Information) through your vendors?
- Ask: Have you ever received a “Right to be Forgotten” request, and did you successfully execute it?
- Verify: Check their architectural diagrams for privacy controls (encryption, access segregation).
3. The “Phish-Prone” Assessment
Test the culture, not just the policy.
- Ask: What is your current click rate on internal phishing simulations?
- Ask: How do you handle repeat offenders?
- Verify: Review their incident response logs for “near misses” reported by employees. A high reporting rate is actually a good sign; it means the culture is alert.
Conclusion
The era of separating “business due diligence” from “technical due diligence” is over. In a digital economy, the code is the business.
When you ignore the cyber posture of an acquisition target, you are gambling with your own company’s resilience. You might be buying a market leader, or you might be buying a dormant ransomware infection and a GDPR lawsuit.
By integrating deep dives into Vulnerability Management, Privacy Architecture, and Security Culture into your M&A process, you do more than just avoid risk; you accurately value the asset. A secure, resilient company is worth a premium. A fragile one demands a discount.
Don’t let hidden liabilities devalue your acquisition. Emutare empowers your due diligence with comprehensive Cybersecurity Risk Assessments and IT Auditing that uncover technical debt before you sign. We rigorously evaluate your target’s digital posture through advanced Vulnerability Management and test their security culture with our specialized Awareness Training. Whether identifying silent code vulnerabilities or ensuring regulatory compliance, our experts help you calculate the true cost of the deal. Secure your investment and merge with confidence using Emutare’s tailored cybersecurity solutions.
References
- Google. (2025). M-Trends 2025 Report. https://services.google.com/fh/files/misc/m-trends-2025-en.pdf ↩︎
- Emutare. (2025). Integration of Vulnerability Management with DevOps. https://insights.emutare.com/integration-of-vulnerability-management-with-devops/ ↩︎
- Microsoft. (2019). 2019 Global Cyber Risk Perception Survey. https://www.microsoft.com/en-us/security/blog/wp-content/uploads/2019/09/Marsh-Microsoft-2019-Global-Cyber-Risk-Perception-Survey.pdf ↩︎
- Emutare. (2025). Privacy by Design: Implementation Framework for Modern Organizations. https://insights.emutare.com/privacy-by-design-implementation-framework-for-modern-organizations/ ↩︎
- Ige, G., & Adebayo, P. (2025). The role of cybersecurity in mergers and acquisitions. ResearchGate. https://www.researchgate.net/publication/394475538_THE_ROLE_OF_CYBERSECURITY_IN_MERGERS_AND_ACQUISITIONS ↩︎
- Emutare. (2025). Security Awareness Program Design: Beyond Compliance. https://insights.emutare.com/security-awareness-program-design-beyond-compliance/ ↩︎
Related blog Posts
- Advanced Anti-Phishing Controls and User Training: Building Resilient Cybersecurity Defenses
- Board Reporting on Cybersecurity: What Executives Need to Know
- Multi-Factor Authentication: Comparing Different Methods
- Secrets Management in DevOps Environments: Securing the Modern Software Development Lifecycle
- Zero Trust for Remote Work: Practical Implementation
- DevSecOps for Cloud: Integrating Security into CI/CD
- Customer Identity and Access Management (CIAM): The Competitive Edge for Australian Businesses

