For the past twenty years, the organizational chart of a typical enterprise security team has looked roughly the same. At the top sits the Chief Information Security Officer (CISO), presiding over a centralized fortress of analysts, engineers, and architects. This “Central Command” model was designed for an era when technology was procured, deployed, and managed solely by the IT department.
That era is over.
In 2026, technology acquisition will be democratized. Marketing teams purchase AI-driven analytics platforms with a credit card. HR departments integrate third-party payroll tools via APIs. Sales leaders spin up cloud instances to host demos. The “perimeter” is no longer a network boundary; it is a sprawling, decentralized web of business decisions made by people who are not security professionals.
The centralized CISO model is struggling to keep pace. When every department acts as its own IT shop, a single central security team becomes a bottleneck. They are viewed either as the “Department of No,” blocking innovation to maintain control, or as distant regulators who don’t understand the unique needs of the business units they protect.
To survive this shift, forward-thinking enterprises are evolving. They are moving away from the “Ivory Tower” model of security and embracing a distributed approach. Enter the Business Information Security Officer (BISO).
This role represents the missing link between the technical requirements of the CISO and the operational realities of the business. The BISO is not just a security guard; they are a diplomat, a translator, and a strategic partner embedded directly within the business units.
1. The Driver: The Decentralization of Risk
Why is the BISO role emerging now? The answer lies in the explosion of “Business-Led IT.”
The speed of digital transformation means that business units cannot wait for a six-month security review before adopting a new tool. They need agility. However, this agility often comes with a blind spot. A marketing director might see a SaaS tool as a revenue generator, but they likely do not see the data sovereignty risks or the API vulnerabilities it introduces.
According to the 2024 Microsoft Data Security Index,1 65% of organizations report that employees are using unsanctioned generative AI tools to do their jobs. Furthermore, the report identifies that 40% of data security incidents in 2024 were linked to AI usage, a figure that nearly doubled from the previous year. This data proves that without a human-centric approach that accommodates user workflows, employees will create their own “shadow” paths, rendering traditional controls ineffective. The BISO is the embodiment of this practice.
Without a BISO, the central security team is often fighting a losing battle against “Shadow IT.” They are trying to police a landscape they cannot see.
As we discussed in our article on SaaS Security Posture Management for Critical Business Applications,2 visibility is the first casualty of decentralization. A central team might not know that the Finance team has granted “Read/Write” access to a new budgeting app until a breach occurs.
A BISO embedded within the Finance department changes this dynamic. They are present in the strategy meetings before the software is bought. They can guide the selection process, ensuring that the business gets the speed it needs while the enterprise gets the security it requires. They turn “Shadow IT” into “Managed Business IT.”
2. Defining the Role: The Bridge Builder
It is important to clarify what a BISO is and what it is not.
A BISO is not simply a “mini-CISO” for a smaller department. Nor are they a helpdesk technician. They are senior-level leaders who possess a dual competency: they speak the language of cybersecurity (vulnerabilities, encryption, compliance), and they speak the language of their specific business unit (customer acquisition cost, supply chain velocity, talent retention).
Their primary mandate is contextualization.
A generic security policy might state: “Block all file-sharing sites.” For the Engineering team, this might be acceptable. For the Creative Design team, which needs to send 4GB video files to external agencies daily, this policy is a work-stopper.
A centralized CISO might not see this nuance until the Design team revolts and finds a dangerous workaround. A BISO embedded in the Design unit would identify this friction point immediately. They would champion a secure, sanctioned alternative, ensuring business continuity without compromising risk posture.
Heidrick & Struggles’ 2024 Global Chief Information Security Officer (CISO) Survey3 highlights this trend, noting that modern security leaders are being evaluated more on their ability to “influence and collaborate” than on their technical prowess alone. The BISO is the operational arm of this influence. Google emphasizes that the modern CISO role has transitioned from a technical gatekeeper to a strategic business partner. In their 2024 CISO Perspectives,4 they highlight that security leaders are now judged on their ability to cultivate shared accountability and translate technical threats into business language. This shift prioritizes influence and culture building over siloed control management to secure necessary board buy-in.
3. Equipping the BISO: The Toolkit for Distributed Defense
For a BISO to be effective, they cannot be an island. They need a tether back to the “Mothership” (the central security strategy). This requires a specific set of tools and workflows that enable communication and decision-making.
The Communication Layer: ChatOps
A BISO embedded in a sales organization cannot spend their day logging tickets in a cumbersome IT portal. They need to operate at the speed of sales.
This is where ChatOps becomes the critical connective tissue. As we detailed in ChatOps for Security Teams: Enhancing Collaboration,5 integrating security workflows into platforms like Slack or Microsoft Teams allows the BISO to bridge the gap between their business unit and the central SOC.
Imagine a scenario where a BISO in the HR department receives a question about a suspicious email. Instead of forwarding it to a generic inbox, they can drop it into a dedicated ChatOps channel where automation instantly analyzes the headers and returns a verdict. The BISO can then communicate that verdict to the HR team in real-time.
ChatOps allows the BISO to leverage the heavy-lifting capabilities of the central SOC without being physically present in the SOC. It keeps them connected to the broader threat landscape while remaining focused on their specific business vertical.
The Persuasion Layer: Threat Intelligence
The BISO’s greatest challenge is often cultural: convincing a profit-driven business leader to spend budget on risk mitigation.
“Because the policy says so” is rarely a compelling argument for a VP of Sales. “Because this specific threat actor is targeting our competitors’ CRM data” is a much stronger one.
To make these arguments, the BISO relies on targeted Threat Intelligence.
In our framework for Measuring ROI of Threat Intelligence Programs,6 we emphasized that intelligence must drive business decisions. The BISO is the primary consumer of this intelligence. They take the raw data provided by the central team, such as a rise in ransomware targeting supply chains, and translate it into a business case for the Supply Chain VP.
They can quantify the risk: “If we don’t patch this vulnerability in our logistics software, the intelligence suggests a 30% probability of disruption this quarter, costing us $X in delayed shipments.” This transforms security from a technical cost into a business investment.
4. The Cultural Shift: From Policing to Partnering
The ultimate goal of the BISO model is to change the culture of the organization.
In the old model, security was something that was “done to” the business. The security team scanned, blocked, and penalized. This created an adversarial relationship where business units would try to hide their activities to avoid scrutiny.
In the BISO model, security is “done with” the business. Because the BISO sits next to the developers, the marketers, or the traders, they build psychological safety.
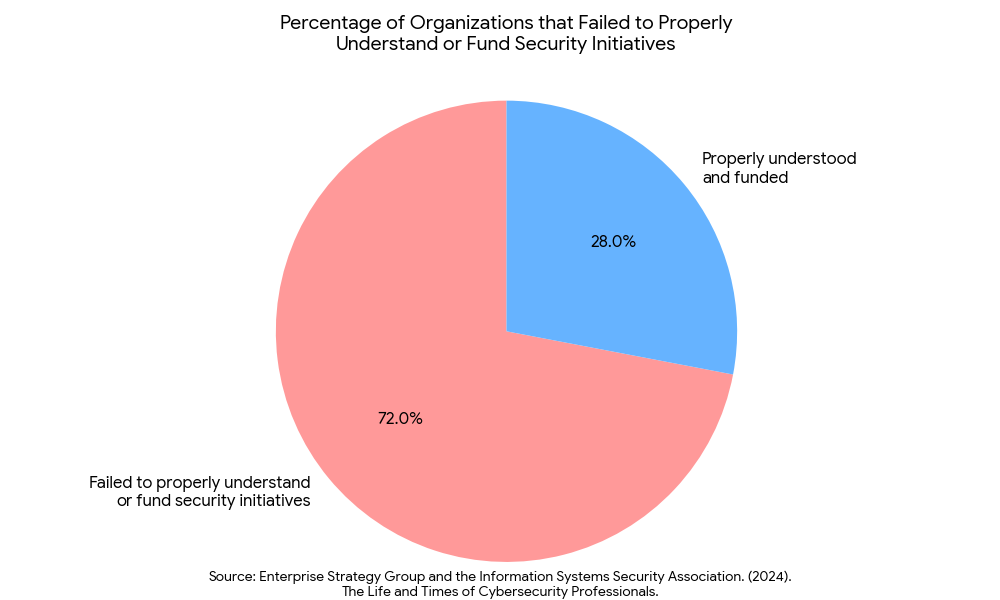
Research from ISSA and ESG, The Life and Times of Cybersecurity Professionals,7 confirms that the disconnect between business leadership and security teams is a major catalyst for burnout. Their data reveals that a good percentage of professionals cite “working with disinterested business managers” as a top stressor, while 72% report working in organizations that failed to properly understand or fund security initiatives. The BISO fixes this alignment. When a developer makes a mistake that introduces a vulnerability, they are more likely to confess it to the BISO they drink coffee with than to a faceless auditor in headquarters.
This cultural shift leads to “Security by Design.” With a BISO in the room, security requirements are written into the project charter from Day One, rather than being bolted on just before launch.
5. Implementation Guidance: Deploying the BISO Model
Transitioning to a distributed BISO model is a significant organizational change. It should be approached in phases.
Phase 1: Identify the Risk Centers
Do not try to place a BISO in every department immediately.
- Analyze Risk: Which business units have the highest “Shadow IT” spend? Which handles the most sensitive data? Usually, this is R&D (Engineering) and Finance.
- Start Here: deploy your first BISOs to these high-risk, high-value units.
Phase 2: The “Ambassador” Pilot
If you do not have the budget for full-time BISOs yet, start with “Security Ambassadors” or “Champions.”
- Select Champions: Identify existing employees within the business units who have an aptitude for security (e.g., a lead developer or a compliance-aware HR manager).
- Empower Them: Give them direct access to the central security team via ChatOps channels and involve them in weekly threat briefings.
Phase 3: Unify the Tooling
Ensure the distributed team is not creating data silos.
Central Visibility: Even though BISOs operate independently, they must use the same SaaS Security Posture Management tools as the central team. The BISO configures the policy for their unit, but the central CISO retains global visibility.
- Shared Intelligence: Create a feedback loop where BISOs feed “ground truth” (what is actually happening in the business) back into the central Threat Intelligence platform.
Conclusion
The complexity of the modern digital enterprise has outgrown the centralized command-and-control model. As businesses race to adopt AI, cloud, and SaaS technologies to gain a competitive edge, the gap between “Central Security” and “The Business” continues to widen.
The BISO is the bridge across that gap.
By embedding security leadership directly into the business units, organizations can achieve the best of both worlds: the agility of decentralized innovation and the resilience of enterprise-grade security.
However, the success of a BISO relies on more than just a job title. It requires the right infrastructure. They need ChatOps to collaborate at speed, SaaS Security tools to gain visibility, and Threat Intelligence to articulate value.
Bridging the gap between business innovation and security requires more than just a new role; it demands the right partners. Emutare empowers your transition to a distributed security model with expert Cybersecurity Governance and Advisory services. We help you navigate the risks of AI Adoption and Shadow IT through tailored consultation and actionable Threat Intelligence. From defining robust frameworks to implementing resilient infrastructure, our team ensures your BISO strategy delivers both agility and protection. Let Emutare equip your organization to turn decentralized risk into a competitive advantage
References
- Microsoft. (2024). Microsoft Data Security Index Annual Report Highlights Evolving Generative Ai Security Needs. https://www.microsoft.com/en-us/security/blog/2024/11/13/microsoft-data-security-index-annual-report-highlights-evolving-generative-ai-security-needs/ ↩︎
- Emutare. (2025). SaaS Security Posture Management for Critical Business Applications. https://insights.emutare.com/saas-security-posture-management-for-critical-business-applications/ ↩︎
- Heidrick & Struggles (2024). 2024 Global Chief Information Security Officer (CISO) Survey. https://www.heidrick.com/-/media/heidrickcom/publications-and-reports/2024-global-ciso-organization-and-compensation-survey.pdf ↩︎
- Google. (2024). Cloud CISO Perspectives: Our 2024 Cybersecurity Forecast report. https://cloud.google.com/blog/products/identity-security/cloud-ciso-perspectives-our-2024-cybersecurity-forecast-report ↩︎
- Emutare. (2025). ChatOps for Security Teams: Enhancing Collaboration. https://insights.emutare.com/chatops-for-security-teams-enhancing-collaboration/ ↩︎
- Emutare. (2025). Measuring ROI of Threat Intelligence Programs: A Strategic Framework for Australian Organizations. https://insights.emutare.com/measuring-roi-of-threat-intelligence-programs-a-strategic-framework-for-australian-organizations/ ↩︎
- Enterprise Strategy Group and the Information Systems Security Association. (2024). The Life and Times of Cybersecurity Professionals. https://www.issa.org/wp-content/uploads/2024/11/eBook-The-Life-and-Times-of-Cybersecurity-Professionals-Volume-VII-2024.pdf ↩︎
Related Blog posts
- APRA CPS 234: Compliance Guide for Financial Institutions
- SOC 2 Compliance: Preparation and Audit Process
- Azure Security Best Practices for Australian Businesses: A Comprehensive Guide for 2025
- Tabletop Exercises: Testing Your Incident Response Plan
- BGP Security: Protecting Your Internet Routing
- Data-Centric Security Architecture: Building Resilience Through Data-Focused Protection
- Network Security Zoning and Segmentation Design: Building Resilient Digital Perimeters in 2025

