For nearly two decades, the cybersecurity industry has chased a specific utopian vision: the “Single Pane of Glass.”
The promise was seductive in its simplicity. Vendors assured Chief Information Security Officers (CISOs) that if they just bought enough modules from a single platform, every alert, log, and vulnerability would appear on one pristine dashboard. The chaos of the Security Operations Center (SOC) would be tamed, and visibility would be absolute.
In 2026, we must admit a hard truth: the Single Pane of Glass is a myth. And for many organizations, chasing it has become a liability.
The reality of modern enterprise IT is not consolidation; it is fragmentation. The average enterprise now manages dozens of distinct security tools, a number that continues to rise as SaaS adoption explodes. Attempts to force all this telemetry into a single proprietary dashboard often result in a “frankensystem,” expensive, sluggish, and riddled with blind spots.
Instead of trying to consolidate everything into one tool, resilient organizations are learning to collaborate across many. They are building a “Unified Collaboration Layer” that prioritizes workflow over dashboards.
1. The Trap of the Monolith: Why Consolidation Fails
The drive for consolidation often stems from “tool fatigue.” When a SOC analyst has to toggle between a firewall console, an Endpoint Detection and Response (EDR) system, and an email gateway, efficiency drops. The industry’s answer was to build massive, monolithic platforms, SIEMs, and XDRs that promised to ingest everything.
However, this approach has created two critical risks: Mediocrity and Vendor Lock-in.
The “Jack of All Trades” Problem
Microsoft’s defense strategy fundamentally argues that attackers do not break into tools; they break into the gaps between them. While a niche vendor might offer a statistically superior specific detection capability, Microsoft claims that a fragmented stack creates “blind spots” that disjointed tools cannot cross-reference, as seen in New Microsoft e-book: 3 reasons point solutions are holding you back.1
In the complex world of cloud applications, “good enough” is often where the breaches happen. As we explored in our guide to SaaS Security Posture Management for Critical Business Applications,2 specific environments like Salesforce or Microsoft 365 require deep, granular visibility that generalist platforms often miss. If your “Single Pane of Glass” simplifies data by stripping away context, it isn’t helping you see; it’s helping you ignore.
The Single Point of Failure
Furthermore, relying on a monolithic vendor creates a dangerous single point of failure. If your endpoint protection, identity management, and threat intelligence are all sourced from Provider X, and Provider X suffers a catastrophic outage (a scenario the industry has witnessed repeatedly in recent years), your entire defensive posture goes dark.
The Australian Cyber Security Centre (ACSC) released comprehensive guidance in 2024 and 2025, Foundations For Modern Defensible Architecture,3 advocating for a “Modern Defensible Architecture” (MDA). This strategic framework champions a “secure-by-design” and “layered” approach where security is not a perimeter wall but a distributed set of controls integrated into every level of the environment, specifically identity, device, network, application, and data. Similar to CSMA, MDA pushes organizations away from disjointed legacy setups toward a flexible, zero-trust-based ecosystem where components are distinct yet work together to verify distinct “confidence signals” before granting access.
2. The Real Solution: A Unified Collaboration Layer
If we cannot force every tool into one dashboard, how do we solve the “swivel chair” problem? The answer lies in changing where the work happens.
We don’t need a single pane of glass (viewing); we need a single pane of glass (doing). This is the philosophy behind ChatOps.
By moving the “action layer” into collaboration platforms like Slack or Microsoft Teams, you create a virtual war room that overlays your fragmented tools. An alert from your best-of-breed EDR and an alert from your specialized SaaS security tool can both land in the same channel.
As we detailed in ChatOps for Security Teams: Enhancing Collaboration,4 this integration does something a dashboard cannot: it brings the human into the loop immediately.
In a traditional setup, an analyst sees an alert on a dashboard, copies the IP address, opens a ticket, emails a system administrator, and waits. In a ChatOps model, the alert arrives in the channel with context already attached. The analyst can tag the system administrator instantly or even execute a command to block the IP directly from the chat window.
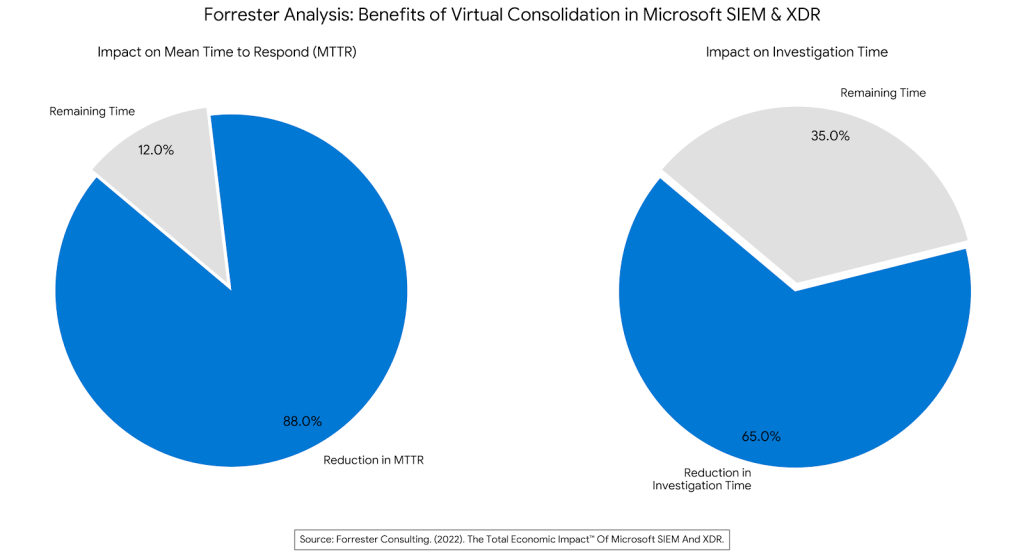
Forrester’s analysis in The Total Economic Impact™ Of Microsoft SIEM And XDR5 confirms that “virtual consolidation” significantly outperforms isolated tools. By integrating separate detection layers into a single response platform, organizations achieved an 88% reduction in Mean Time to Respond (MTTR).
The study found that this unified workflow eliminated the friction of screen-switching, cutting investigation time by 65%.
3. Strategic Flexibility: The ROI of Being Agnostic
Moving away from the “Single Pane” myth also has profound economic benefits. It restores leverage to the buyer.
When you are locked into a monolithic platform, switching costs are astronomical. You are effectively held hostage by that vendor’s pricing model and roadmap. If they decide to deprioritize a feature you rely on, you have no recourse.
A “collaboration-first” architecture is vendor-agnostic. You can subscribe to a specialized Threat Intelligence feed for a specific geopolitical region without worrying if it “natively integrates” with your SIEM. As long as it has an API that can feed your collaboration layer, it is valuable.
This aligns perfectly with the framework we established in Measuring ROI of Threat Intelligence Programs.6 The value of intelligence is not that it sits in a pretty dashboard; the value is that it drives a decision.
By decoupling your data sources from your visualization tools, you can invest in high-fidelity intelligence that specifically targets your industry’s risks. You can choose the best SaaS security tool for your marketing apps and the best network tool for your data center. You are building a resilient ecosystem, not buying a pre-packaged box.
4. Implementation Guidance: Building the Mesh
For leaders ready to abandon the “Single Pane” chase, the transition to a collaboration-centric model can be achieved in three phases.
Phase 1: Audit Your Integrations
Stop asking “Does Tool A talk to Tool B?” and start asking “Do Tool A and Tool B talk to my Team?”
- Identify the Silos: Map out which tools require your analysts to log in separately. These are your friction points.
- API Readiness: Ensure your “best-of-breed” tools have robust, open APIs. If a vendor blocks you from extracting your own data to force you into their dashboard, they are a legacy liability.
Phase 2: Establish the Collaboration Hub
Treat your chat platform as a security tool.
- Centralize Alerts: Use webhooks or dedicated bots to route high-priority alerts into specific channels (e.g., #sec-ops-critical).
- Enrich Automatically: Don’t just dump raw logs. Configure your automation to look up reputation scores or user details and append them to the alert before it hits the chat.
Phase 3: The “Federated” Dashboard
If you must have a dashboard, build one that aggregates metrics, not operations.
- Business Views: specialized tools can feed into a lightweight BI (Business Intelligence) tool for executive reporting. The CISO needs a single view of risk, but the analyst does not need a single view of configuration. Keep those layers separate.
Conclusion
The “Single Pane of Glass” was a dream born in an era of on-premise, perimeter-based networks. In the decentralized, API-driven world of 2026, it is an anachronism.
Complexity in cybersecurity is inevitable. The goal is not to hide that complexity behind a simplified dashboard, but to manage it through superior collaboration. By embracing a strategy that favors best-of-breed tools connected by a Unified Collaboration Layer (ChatOps), organizations can achieve true agility.
We must stop looking for a magical window that sees everything, and start building a team that can respond to anything, regardless of which tool detects it.
Stop chasing the Single Pane of Glass myth. Emutare helps you build the resilient ecosystem your security team needs. Through our Cybersecurity and IT Infrastructure Architecture Development and AI-Driven Process Automation, we move you from passive dashboards to active collaboration. Our expert Cybersecurity Advisory services ensure your distinct tools work together effectively instead of creating silos. Don’t let vendor lock-in dictate your defense. Let us design a Modern Defensible Architecture that turns fragmentation into your strength. Partner with Emutare to unify your operations and prioritize action over observation
References
- Microsoft. (2025). New Microsoft e-book: 3 reasons point solutions are holding you back. https://www.microsoft.com/en-us/security/blog/2025/12/18/new-microsoft-e-book-3-reasons-point-solutions-are-holding-you-back/ ↩︎
- Emutare. (2025). SaaS Security Posture Management for Critical Business Applications. https://insights.emutare.com/saas-security-posture-management-for-critical-business-applications/ ↩︎
- Australian Cyber Security Centre (ACSC). (2025). Foundations For Modern Defensible Architecture. https://www.cyber.gov.au/business-government/secure-design/secure-by-design/modern-defensible-architecture/foundations-for-modern-defensible-architecture ↩︎
- Emutare. (2025). ChatOps for Security Teams: Enhancing Collaboration. https://insights.emutare.com/chatops-for-security-teams-enhancing-collaboration/ ↩︎
- Forrester Consulting. (2022). The Total Economic Impact™ Of Microsoft SIEM And XDR. https://dmc.partner.microsoft.com/cdn/assets/55e05d26-08fa-4e3b-8309-3e627864522f/content/TEI%20ofMicrosoftSIEMandXDR%20-%20Week%205_23063020484744.pdf ↩︎
- Emutare. (2025). Measuring ROI of Threat Intelligence Programs: A Strategic Framework for Australian Organizations. https://insights.emutare.com/measuring-roi-of-threat-intelligence-programs-a-strategic-framework-for-australian-organizations/ ↩︎
Related Blog posts
- Threat Intelligence Sharing: Communities and Frameworks
- Healthcare Information Security: Australian Privacy Requirements
- Cost-Effective Security Solutions for Limited Budgets
- Threat Hunting: Methodologies and Tools
- Email Data Loss Prevention Strategies: A Comprehensive Guide for Australian Organizations
- Alert Fatigue: Strategies for Effective Prioritization
- Social Engineering: Beyond Phishing – Unmasking the Human Element in Cyber Attacks

