It is a scenario that plays out in corporate headquarters every Friday afternoon. An employee resigns, or perhaps they are let go. The HR team processes the paperwork, conducts an exit interview, and notifies IT. At 5:00 PM sharp, the IT administrator clicks a button in Active Directory or Okta, disabling the user’s primary account. The laptop is returned, the badge is deactivated, and the building access is revoked.
The organization believes the perimeter is secure. They are wrong.
In the modern digital enterprise, the physical employee has left the building, but their digital ghost remains. They are still logged into the CRM via a session token on their personal tablet. Their API keys are still hardcoded into a private repository. The third-party project management tool they signed up for with a corporate email, but without IT’s knowledge, is still active, holding gigabytes of sensitive intellectual property.
We have entered an era where offboarding is the new perimeter. The assumption that a single “kill switch” in an Identity Provider (IdP) can sever all access is a dangerous fallacy. As SaaS sprawl accelerates and “Shadow IT” becomes the norm, the gap between an employee leaving and their access actually ceasing has become the most fertile ground for insider threats.
1. The “Kill Switch” Myth: Why SSO Is Not Enough
For years, the industry relied on Single Sign-On (SSO) as the silver bullet for access management. The logic was sound: if all roads lead through one gate, locking that gate should secure the castle. However, the reality of 2025 is that the castle has no walls, and the roads are infinite.
Zylo’s 2025 SaaS Management Index shows that the average enterprise now maintains approximately 275 distinct SaaS applications. Crucially, IT teams directly oversee only a good percentage of this spend. Verizon’s 2025 Mobile Security Index1 also reveals that 93% of organizations report that employees are now using generative AI applications on mobile devices. Crucially, only 17% have implemented specific security controls to oversee this emerging technology. The vast majority of these applications are adopted by business units, marketing, HR, and engineering, often without a formal security review.
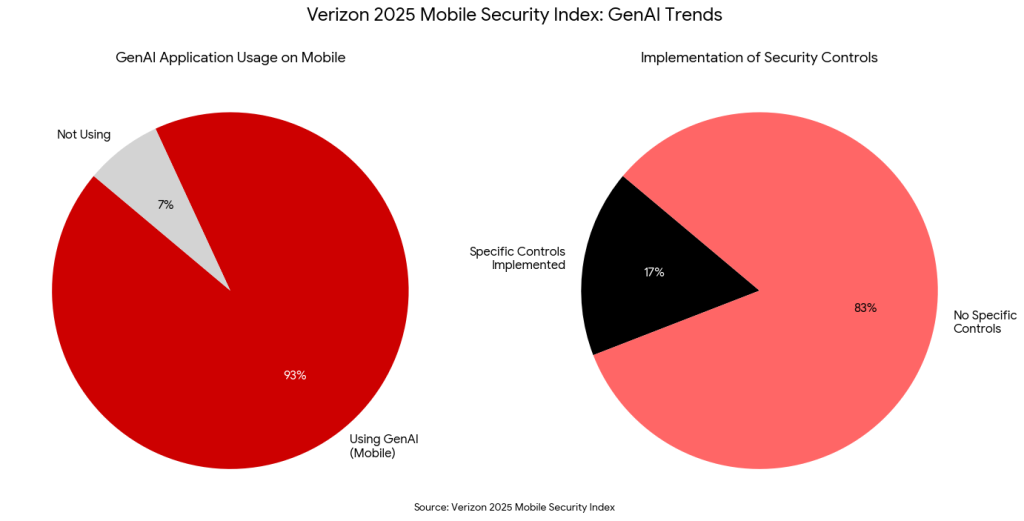
When an employee leaves, IT disables the accounts they know about. But what about the ones they don’t?
Cisco’s 2025 Cybersecurity Readiness Index2 highlights a critical oversight in the “digital estate”: 84% of companies report that employees access corporate platforms from unmanaged devices, which are often invisible to IT security teams. Consequently, only 4% of organizations worldwide have achieved a “Mature” level of readiness to defend against identity-based attacks and insider threats.
This creates a phenomenon known as “Zombie Accounts.” These are valid user accounts that belong to humans who no longer work for the company. They are not monitored because they are often outside the SSO umbrella. If a former sales director logs into a niche lead-generation tool two weeks after being fired, using a password they set locally, your expensive SIEM (Security Information and Event Management) system will likely not generate a single alert.
To combat this, organizations must move beyond the “Kill Switch” mentality and adopt a posture of continuous discovery. As we explored in our guide to SaaS Security Posture Management for Critical Business Applications,3 visibility is the precursor to control. You cannot revoke what you cannot see. A resilient offboarding strategy requires tools that can scan the environment for all identities, managed and unmanaged, and map them back to HR status in real-time.
2. The Shadow Perimeter: API Keys and OAuth Tokens
The risk of the ex-employee extends far beyond simple login credentials. In a hyper-connected ecosystem, users grant access to things as often as they grant access to people.
Consider a developer who connects a third-party code linter to your private GitHub repository. To do this, they grant an OAuth token, a digital key that allows that third-party tool to read your code. When that developer leaves the company and their email is disabled, the OAuth token often remains valid. If that third-party tool is compromised months later, the attackers can ride that valid token straight into your environment.
This is not a theoretical edge case. The Australian Cyber Security Centre’s (ACSC) Annual Cyber Threat Report 2023-20244 highlighted that 32% of critical infrastructure incidents are now caused by compromised accounts or credentials. The report notes that organizations are struggling to monitor non-human identities, which persist long after the human has departed.
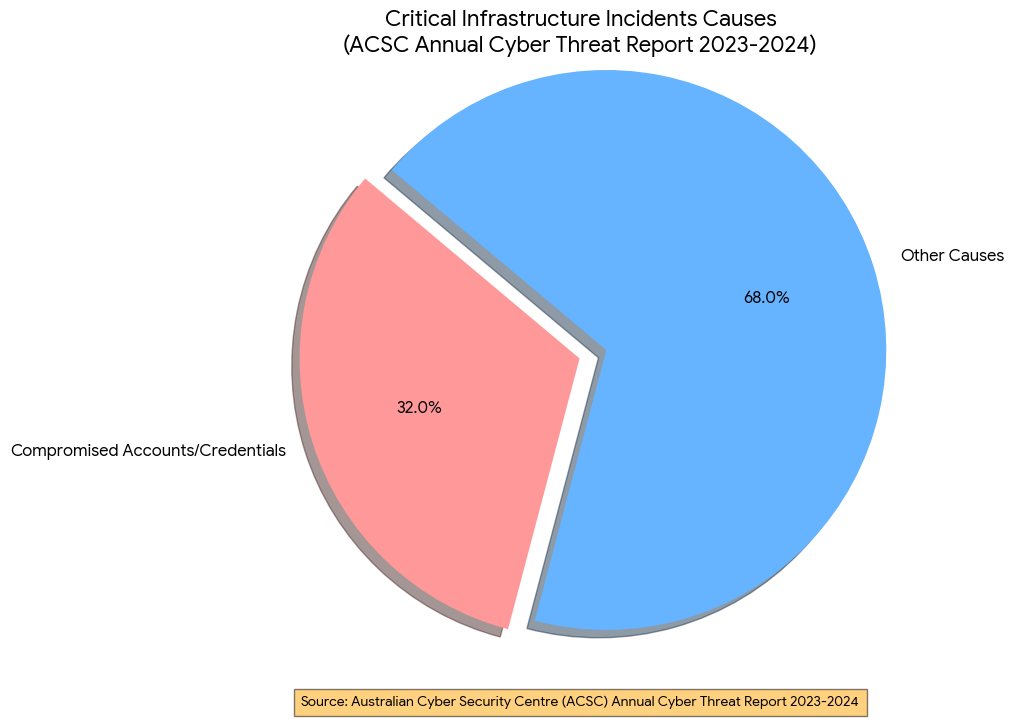
This “Shadow Perimeter” of API keys, personal access tokens (PATs), and integration secrets is invisible to traditional offboarding checklists. A manual spreadsheet tracking “who has a laptop” cannot capture the complex web of API permissions a senior engineer creates over a three-year tenure.
Operationalizing the Clean-Up
This is where operational speed becomes a security feature. The lag time between HR notifying IT and IT revoking these complex permissions is the “danger zone.”
To close this gap, forward-thinking teams are utilizing ChatOps to orchestrate the offboarding workflow. As we detailed in ChatOps for Security Teams: Enhancing Collaboration,5 modern security requires breaking down the silos between departments.
Imagine a workflow where the moment an HR representative updates a status to “Terminated” in the HRIS (Human Resources Information System), a secure bot in the IT Slack channel automatically triggers a playbook. This playbook doesn’t just disable the Active Directory account; it rotates the API keys associated with that user, revokes their active OAuth tokens, and scans for any “orphan” accounts in non-SSO apps linked to their email.
By automating this process via ChatOps, you remove the human latency. You ensure that the digital exit happens simultaneously with the physical one.
3. The Economic Justification: The ROI of Zero Trust Offboarding
For business leaders, the question often boils down to cost. Investing in advanced SaaS Security Posture Management (SSPM) and automated offboarding tools requires a budget. However, the cost of inaction is exponentially higher.
Verizon’s 2025 Data Breach Investigations Report6 (DBIR) provides a sobering financial reality. The report indicates that the “human element” is involved in 60% of all breaches.5 More alarmingly, breaches involving insider threats (which include disgruntled ex-employees) have seen a sharp rise in cost.
When an ex-employee takes proprietary data, customer lists, pricing models, or source code to a competitor, the damage is rarely immediate. It manifests quarters later in lost market share and eroded competitive advantage. Measuring this risk is critical for securing the budget needed to mitigate it.
We previously discussed frameworks for this in our article on Measuring ROI of Threat Intelligence Programs.7 The same principles apply here. To calculate the ROI of a robust offboarding program, CISOs should model the “Impact of Data Exfiltration.”
If your organization holds intellectual property valued at $10 million, and the probability of an improperly offboarded employee retaining access is 20% (as suggested by the Folks RH stats), the Annualized Loss Expectancy (ALE) is significant. By implementing a system that reduces that probability to near zero, the ROI is immediate and defensible in the boardroom.
Furthermore, regulatory bodies are beginning to crack down on “orphan accounts.” Under frameworks like GDPR and the Australian Privacy Act, holding personal data in an account that no one monitors is a compliance violation. The fines associated with these violations further bolster the economic case for automated offboarding.
4. Implementation Guidance: Closing the Gap
For leaders looking to secure the “New Perimeter,” we recommend a three-phased approach to modernizing the offboarding process.
Phase 1: The Discovery Audit
You must identify the scope of the problem.
- Shadow SaaS Scan: Use a CASB (Cloud Access Security Broker) or SSPM tool to scan for all applications being accessed by corporate emails. Compare this list against your known SSO inventory. The difference represents your “Offboarding Gap.”
- Integration Review: Audit your core platforms (Google Workspace, Microsoft 365, Salesforce, Slack) for third-party apps installed by users. Look for apps installed by users who are no longer on the payroll.
Phase 2: The Integration of HR and IT
Security cannot be the last to know.
- Sync Systems: Ensure your HRIS is the “source of truth.” IT should not be waiting for an email ticket to begin offboarding.
- Automate the Trigger: Implement a script or bot (via ChatOps) that listens for status changes in the HR system and immediately initiates the “Revoke” protocols.
Phase 3: The Deep Clean
Go beyond the login.
- Revoke Tokens: Your offboarding checklist must include the revocation of API keys, OAuth tokens, and browser sessions.
- Transfer Data: Automate the transfer of data (Google Drive files, CRM records) from the exiting user to a manager before deletion to prevent business continuity issues.
- Continuous Monitoring: Set up alerts for “Zombie Activity.” Any login attempt by a deactivated user’s credentials should be treated as a Sev-1 security incident.
Conclusion
The traditional perimeter was built of firewalls and badge readers. The new perimeter is composed of identities, permissions, and trust. When an employee leaves, that trust is revoked, but without the right tools, the permissions often remain.
The statistics from 2024 and 2025 are clear: the “Insider Risk” is no longer just about malicious spies; it is about negligence and the complexity of the modern SaaS stack. An ex-employee with a valid session token is just as dangerous as a hacker with a zero-day exploit, perhaps more so, because they know exactly where your most valuable data lives.
By embracing total visibility through SaaS security posture management, increasing operational speed through ChatOps, and justifying the strategy through clear ROI models, organizations can close the offboarding gap. We can ensure that when an employee says goodbye, their access truly says goodbye to them.
Stop digital ghosts from lingering in your network. Emutare closes the offboarding gap through comprehensive IT Asset Management and AI-Driven Process Automation. We help you identify “Shadow IT” and orchestrate instant access revocation for seamless transitions. Our Cybersecurity Governance experts further strengthen your defense by aligning policies with regulatory standards to mitigate insider threats. Don’t rely on a simple kill switch when you can have total visibility and control. Secure your new perimeter with Emutare.
References
- Verizon. (2025). 2025 Mobile Security Index. https://www.verizon.com/business/resources/T550/reports/2025-mobile-security-index.pdf ↩︎
- Cisco. (2025). 2025 Cisco Cybersecurity Readiness Index. https://newsroom.cisco.com/c/dam/r/newsroom/en/us/interactive/cybersecurity-readiness-index/2025/documents/2025_Cisco_Cybersecurity_Readiness_Index.pdf ↩︎
- Emutare. (2025). SaaS Security Posture Management for Critical Business Applications. https://insights.emutare.com/saas-security-posture-management-for-critical-business-applications/ ↩︎
- Australian Signals Directorate (ASD). (2024). Annual Cyber Threat Report 2023-2024. Australian Cyber Security Centre (ACSC). https://www.cyber.gov.au/about-us/view-all-content/reports-and-statistics/annual-cyber-threat-report-2023-2024 ↩︎
- Emutare. (2025). ChatOps for Security Teams: Enhancing Collaboration. https://insights.emutare.com/chatops-for-security-teams-enhancing-collaboration/ ↩︎
- Verizon. (2025). 2025 Data Breach Investigations Report. https://www.verizon.com/business/resources/Tbb1/reports/2025-dbir-data-breach-investigations-report.pdf ↩︎
- Emutare. (2025). Measuring ROI of Threat Intelligence Programs: A Strategic Framework for Australian Organizations. https://insights.emutare.com/measuring-roi-of-threat-intelligence-programs-a-strategic-framework-for-australian-organizations/ ↩︎
Related Blog Posts
- SaaS Security Posture Management for Critical Business Applications
- Measuring ROI of Threat Intelligence Programs: A Strategic Framework for Australian Organizations
- Your People, Your Shield: A Guide to Security Awareness for Small Business Employees
- Navigating the Digital Maze: A Guide to Log Management Best Practices for Australian Compliance
- ChatOps for Security Teams: Enhancing Collaboration
- Directory Services Security: Active Directory and Beyond
- IDS/IPS Deployment Strategies for Maximum Effectiveness

