In the early days of cybersecurity, the prevailing wisdom was simple: build a wall high enough to keep the bad actors out. The strategy was binary; secure or insecure, safe or breached. But as we move deeper into the latter half of the decade, that binary worldview has collapsed. The perimeter has not just dissolved; it has expanded into an infinite, nebulous web of third-party applications, cloud instances, and remote endpoints.
We have entered the era of the “Resilient by Design” enterprise.
According to the World Economic Forum’s Global Cybersecurity Outlook 2025,1 the landscape has shifted dramatically. Cyber resilience is no longer just a technical objective; it is a critical business enabler in a world defined by geopolitical instability and rapid technological complexity. The report highlights that supply chain vulnerabilities are now the top ecosystem risk for large organizations, with 54% identifying it as their primary barrier to resilience.
This signals a fundamental change in the CISO’s mandate. The goal is no longer solely prevention, as total prevention is a statistical impossibility. The goal is resilience—the ability to withstand, recover from, and adapt to adverse conditions. Achieving this state of resilience requires a tripartite strategy: Visibility into your expanding digital footprint, Speed in your operational response, and Intelligence to justify your strategic direction.
In this article, we will explore how modern enterprises can unify these three pillars, specifically focusing on SaaS security, ChatOps, and Threat Intelligence ROI, to build an organization that is not just secure, but resilient by design.
1. The Visibility Crisis: Why Confidence Does Not Equal Safety
The first pillar of resilience is visibility. You cannot secure what you cannot see, and unfortunately, most organizations are seeing far less than they believe.
The explosion of Software-as-a-Service (SaaS) applications has democratized technology adoption. Marketing teams can spin up analytics platforms, HR can deploy engagement tools, and developers can integrate new libraries, all without a single ticket to the IT helpdesk. While this agility drives business growth, it creates a massive “Shadow IT” blind spot that adversaries are eager to exploit.
Recent data paints a concerning picture of this visibility gap. The 2024 Cybersecurity Readiness Index by Cisco2 reveals a startling paradox: while 80% of organizations expressed moderate to high confidence in their ability to defend against cyberattacks, only 3% possess the “Mature” level of readiness required to actually do so. This “Readiness Gap” suggests that security leaders are mistaking the purchase of multiple security tools for the integrated resilience needed to withstand modern threats.
The SaaS Attack Surface
The risks here are not theoretical. They stem from misconfigurations, over-privileged accounts, and third-party integrations that retain access long after they are needed. When a marketing automation tool is compromised, it is not just email addresses at risk; it is often a lateral pathway into the core corporate network.
To learn more about securing these critical environments, we previously covered the nuances of SaaS Security Posture Management for Critical Business Applications.3 In that analysis, we discussed how manual audits are insufficient in a world where configurations drift daily. A resilient enterprise must replace periodic checks with continuous automated monitoring.
The disconnect between confidence and reality often stems from the nature of modern attacks. Adversaries do not always “hack” in; they log in. They utilize valid credentials harvested from one unmonitored SaaS platform to pivot into another. If your resilience strategy does not explicitly include a framework for governing SaaS sprawl, your perimeter is effectively porous.
2. The Need for Speed: Breaking Operational Silos
The second pillar of resilience is speed. Once a threat is visible, the clock starts ticking. In the industry, we measure this via Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR).
The statistics regarding response times are sobering. According to industry analysis from IBM and Ponemon Institute, the average time to identify and contain a data breach has hovered around 277 days. Imagine the damage an adversary can do with nearly nine months of dwell time inside a network. They can map infrastructure, exfiltrate intellectual property, and plant backdoors that persist even after the initial vulnerability is patched.
Why are response times so slow? The answer often lies in the “human element” and operational friction.
The Human Element and Alert Fatigue
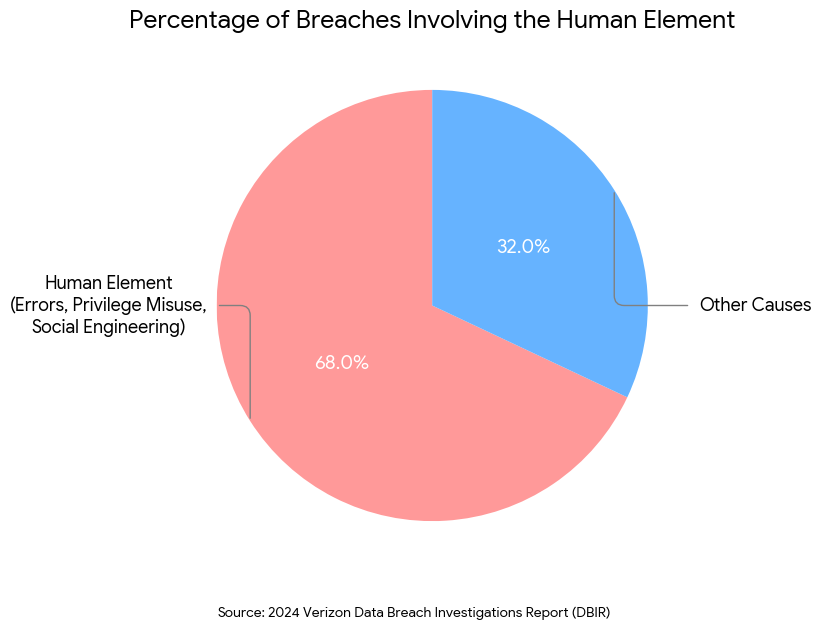
The2024 Verizon Data Breach Investigations Report (DBIR)4 notes that the human element was involved in 68% of breaches, spanning errors, privilege misuse, and social engineering. But the human element is also the bottleneck in defense. Security Operations Centers (SOCs) are often inundated with alerts. Analysts must switch between dozens of dashboards, SIEM, EDR, email security, and ticketing systems — to contextually understand a single alert. This “context switching” carries a heavy cognitive load and slows down decision-making.
This is where the concept of ChatOps becomes transformative. By moving security operations into the collaboration platforms where teams already work (such as Slack or Microsoft Teams), organizations can dramatically reduce friction.
As we detailed in our guide on ChatOps for Security Teams: Enhancing Collaboration,5 ChatOps is not just about convenience; it is about operational velocity. When an alert flows directly into a dedicated channel, enriching itself automatically with threat intel data, the relevant stakeholders can swarm the issue immediately. There is no waiting for an email, no logging into a separate portal to retrieve a log file, and no ambiguity about who is handling the ticket.
A resilient enterprise recognizes that time is the most critical currency in a cyber incident. By integrating ChatOps, you are effectively removing the administrative latency that allows attackers to burrow deeper into the network.
3. The Strategic Justification: Proving the Value of Resilience
The third pillar is arguably the most difficult for technical leaders: Intelligence and Economic Justification.
Building a resilient enterprise requires investment. You need budget for SaaS security tools, budget for automation platforms, and budget for high-quality threat intelligence. However, convincing a CFO to release those funds requires speaking the language of business risk, not just technical vulnerability.
The WEF Global Cybersecurity Outlook 20256 points out a growing divide: the cyber skills gap has increased by 8% since 2024, leaving many organizations understaffed. In this environment, leaders must ensure that every dollar spent delivers maximum efficacy. We cannot simply “hire more people” to solve the problem; we must invest in intelligence that allows our existing teams to focus on the right threats.
moving from Cost Center to Value Protection
However, measuring the return on investment (ROI) for something like Threat Intelligence is notoriously difficult. How do you calculate the value of a breach that didn’t happen?
This is a challenge we addressed comprehensively in our strategic framework for Measuring ROI of Threat Intelligence Programs.7 The key is to shift the metric from “volume of threats blocked” to “strategic impact.”
For instance, if your Threat Intelligence program identifies that a specific threat actor is targeting your industry with a specific SaaS vulnerability, and you patch that vulnerability before exploitation, the ROI is the avoided cost of that breach. With the global average cost of a data breach reaching nearly $4.88 million (according to IBM’s 2024 figures), the math begins to make sense to the board.
A resilient enterprise uses Threat Intelligence not just to block IPs, but to inform business decisions. It answers questions like: Should we expand into this new market given the geopolitical cyber risk? Is this new SaaS vendor secure enough to handle our customer data? When security becomes a decision-support function rather than just a gatekeeper, it achieves true resilience.
4. The Blueprint: Implementation Guidance for Leaders
Understanding the theory of “Resilient by Design” is one thing; implementing it is another. For business leaders and IT professionals looking to bridge the gap between strategy and execution, we recommend the following phased approach.
Phase 1: Audit and Govern the SaaS Estate
You must start by illuminating the shadows.
- Discovery: Use automated tools to scan your network logs and financial records for payments to unknown software vendors. You will likely find 3 to 4 times more applications than you expect.
- Classification: Categorize these applications by risk. A graphic design tool likely poses less risk than an unauthorized PDF converter that has access to your legal documents.
- Policy Implementation: Do not just block everything. Instead, establish a “paved road” policy where secure, approved alternatives are easily accessible to employees.
Phase 2: Operationalize Speed via ChatOps
Stop forcing your analysts to be data entry clerks.
- Integrate: Connect your alerting tools to your collaboration platform. Start with high-fidelity alerts to avoid flooding the channels.
- Automate Context: Configure your bots to automatically pull relevant data (IP reputation, user location, device status) and post it in the thread along with the alert.
- Democratize Response: Allow authorized team members to trigger actions (like “suspend user” or “isolate host”) directly from the chat interface, protected by multi-factor authentication.
Phase 3: Define and Communicate Value
Change the narrative in the boardroom.
- Align Metrics: Stop reporting on “number of attacks blocked.” Start reporting on “Mean Time to Respond” and “Risk Exposure Reduction.”
- Scenario Planning: Use your threat intelligence to run tabletop exercises with executive leadership. Show them a realistic scenario based on current trends (e.g., a supply chain ransomware attack) and walk them through the financial implications.
- Continuous Improvement: Use every incident, major or minor, as a data point to refine your ROI model.
Conclusion
The transition to a “Resilient by Design” enterprise is not a destination; it is a continuous evolution. The threat landscape of 2025 and beyond is characterized by complexity and speed. Adversaries are leveraging AI to craft more convincing phishing campaigns, they are exploiting the interconnectedness of our SaaS supply chains, and they are capitalizing on the fatigue of our defenders.
However, by focusing on the three pillars discussed, Visibility through robust SaaS security, Speed through ChatOps collaboration, and Strategy through measurable Threat Intelligence, organizations can turn the tide.
We can close the confidence gap. We can reduce the dwell time of attackers from months to minutes. And we can demonstrate to our stakeholders that cybersecurity is not just a cost center, but the very foundation upon which modern business innovation is built.
Bridge the gap between confidence and readiness with Emutare. Our Cybersecurity Governance and Advisory services align your security strategy with business value. We illuminate blind spots through Vulnerability Management and Threat Intelligence Reports, ensuring complete visibility of your digital footprint. Enhance your operational speed with our Incident Response Planning and SIEM Deployment to neutralize threats instantly. Build a truly resilient enterprise with Emutare.
References
- World Economic Forum (2025). Global Cybersecurity Outlook 2025. https://reports.weforum.org/docs/WEF_Global_Cybersecurity_Outlook_2025.pdf ↩︎
- Cisco. (2024). 2024 Cisco Cybersecurity Readiness Index. https://newsroom.cisco.com/c/dam/r/newsroom/en/us/interactive/cybersecurity-readiness-index/documents/Cisco_Cybersecurity_Readiness_Index_FINAL.pdf ↩︎
- Emutare. (2025). SaaS Security Posture Management for Critical Business Applications. https://insights.emutare.com/saas-security-posture-management-for-critical-business-applications/ ↩︎
- Verizon. (2024). 2024 Verizon Data Breach Investigations Report. https://www.verizon.com/business/resources/reports/2024-dbir-data-breach-investigations-report.pdf ↩︎
- Emutare. (2025). ChatOps for Security Teams: Enhancing Collaboration. https://insights.emutare.com/chatops-for-security-teams-enhancing-collaboration/ ↩︎
- World Economic Forum (2025). Global Cybersecurity Outlook 2025. https://reports.weforum.org/docs/WEF_Global_Cybersecurity_Outlook_2025.pdf ↩︎
- Emutare. (2025). Measuring ROI of Threat Intelligence Programs. https://insights.emutare.com/measuring-roi-of-threat-intelligence-programs-a-strategic-framework-for-australian-organizations/ ↩︎
Related Blog Posts
- Secure CI/CD Pipelines: Design and Implementation
- Certificate-Based Authentication for Users and Devices: A Comprehensive Security Strategy
- IoT Security Challenges in Enterprise Environments
- Future of IoT Security: Regulations and Technologies
- Risk-Based Authentication: Adaptive Security
- IoT Threat Modeling and Risk Assessment: Securing the Connected Ecosystem
- Red Team vs. Blue Team vs. Purple Team Exercises: Strengthening Your Organization’s Security Posture

