In the rapidly evolving landscape of enterprise cybersecurity, attention is frequently monopolized by the “front door” mechanisms. Security teams and business leaders naturally focus their resources on the shiny new web application, the latest mobile app release, or the newly architected cloud environment. The prevailing assumption suggests that attackers will invariably target these most visible and high-value assets. However, the reality of modern data breaches is often far grimier and considerably less sophisticated than the complex zero-day exploits we fear.
The most significant vulnerability in your enterprise today is likely not a flaw in your cutting-edge software. It is an “obsolete endpoint,” colloquially known as a “Zombie API.” This is an old, deprecated version of an application interface that was supposed to be turned off three years ago but was left running “just in case”. These forgotten endpoints represent the digital undead of the network infrastructure. They receive no security patches, they often bypass modern firewalls, and they frequently lack the strict authentication protocols applied to current production systems. Yet, despite their neglect, they remain connected to your core databases, silently waiting for someone to find them.
For business leaders and IT professionals, addressing the risk of these legacy assets is no longer merely a housekeeping task; it is a critical defense strategy. This article outlines the mechanics of this threat, explores why traditional tools fail to stop it, and provides a comprehensive guide to hunting down and decommissioning these invisible risks.
The Anatomy of a Governance Failure
To understand the threat, we must first understand the lifecycle of an API. In a healthy software environment, an API is developed, released, maintained, and eventually deprecated when a new version takes its place. Ideally, when Version 2, or v2, is released, Version 1, or v1, is given a sunset date and eventually turned off.
In practice, however, fear drives architecture. Developers worry that turning off v1 will break a legacy integration with a key partner or disrupt a critical internal workflow. As a result, v1 is left active. Over time, the team that built v1 leaves the company, documentation is lost, and the endpoint fades into obscurity. It becomes a Zombie.
This phenomenon contributes to what is known as “API Sprawl”. The 2024 Verizon Data Breach Investigations Report1 identifies a massive 180% increase in attacks that exploit vulnerabilities, marking a significant shift in how hackers enter systems. It confirms that web applications and APIs have become the primary “doorway” for breaches, as attackers increasingly target these interfaces to bypass traditional security perimeters.
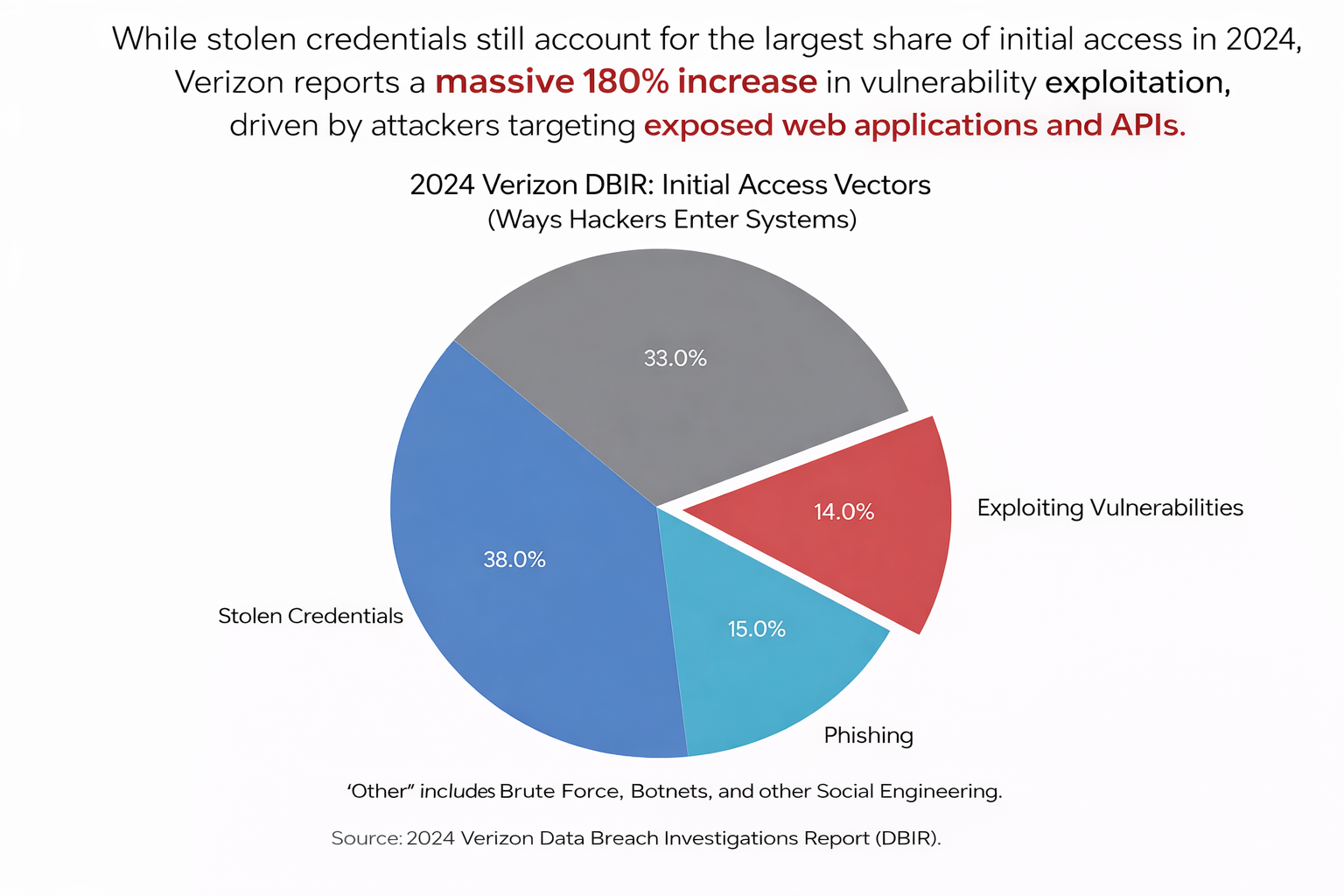
With such massive volume, losing track of individual endpoints is dangerously easy. When an attacker targets an organization, they perform extensive reconnaissance. They do not just look at the standard login paths. They use automated fuzzing tools to scan for api.company.com/v1/login, /beta/login, or even /test/login.
If they find an obsolete endpoint, they have struck gold. These endpoints often lack rate limiting or use outdated encryption, offering a frictionless path to sensitive data.
The Role of CI/CD in Asset Accumulation
Ironically, the very tools designed to speed up development often contribute to the problem of obsolete endpoints. Modern DevOps practices encourage rapid deployment and continuous integration, where code is pushed to production dozens of times a day. However, as we discussed in our guide on Secure CI/CD Pipelines: Design and Implementation,2 the focus of most pipelines is on deployment rather than decommissioning.
Automation scripts are excellent at spinning up new infrastructure, but they rarely include logic to tear down the old. Unless your pipeline explicitly includes “Infrastructure as Code” (IaC) governance that removes obsolete resources, every deployment potentially adds to the pile of unmanaged assets. A developer might spin up a temporary API for a hackathon or a client demo, deploy it via the pipeline, and then move on to the next project. Without a strict “garbage collection” policy in the CI/CD process, that temporary API runs forever, consuming resources and expanding the attack surface.
Hardware Dependencies and the IoT Factor
One of the primary reasons organizations are terrified to kill obsolete APIs is the Internet of Things (IoT). Unlike a mobile app, which can be forced to update via an app store, physical devices are difficult to patch. Consider a smart thermostat or a connected manufacturing sensor deployed five years ago. It was likely hard-coded to communicate with a specific v1 endpoint. If you turn off that v1 endpoint, the device stops working.
This creates a paralysis where security teams are forced to keep insecure endpoints alive to support legacy hardware. We explored the complexities of this hardware-software relationship in our article on IoT Security Challenges in Enterprise Environments.3 The persistence of these devices forces companies to maintain “Shadow APIs” that are kept off the public documentation but are still publicly accessible. Attackers know this. They specifically hunt for IoT-related endpoints because they know these interfaces rarely support modern security standards like Multi-Factor Authentication (MFA) or OAuth 2.0.
The Failure of Traditional Defenses
Why do standard security tools fail to catch these ghosts? Most Web Application Firewalls (WAFs) and API Gateways work on a positive security model regarding known traffic. They protect the APIs you tell them to protect. If an API endpoint is not registered in the gateway, perhaps because it was deployed on a rogue server or a forgotten cloud instance, the WAF does not see it. It is invisible to the defense team but visible to the public internet.
Microsoft’s Building a Comprehensive API Security Strategy4 establishes that complete asset visibility is the absolute foundation of security, explicitly stating that organizations “cannot protect what they do not know exists.” The report warns that relying on manual, static inventories, such as spreadsheets, inevitably leads to outdated information, leaving “shadow” and unmanaged APIs exposed to critical risks like those listed in the OWASP Top 10.5 Consequently, it advocates for a security model based on continuous, automated API discovery to ensure every digital asset is identified, monitored, and secured in real-time throughout its entire lifecycle.
A Strategic Framework for Decommissioning
To eliminate obsolete endpoints, you need a proactive governance strategy. This is not a one-time project but a continuous process. We recommend a four-step framework.
Step 1: The Archaeological Inventory
The first step is to build a dynamic inventory. Do not rely on documentation like Swagger or OpenAPI specs, as it is almost certainly wrong. You need to look at the traffic.
This begins with log analysis. You must aggregate logs from your load balancers, CDNs, and cloud ingress points. Look for traffic hitting URI paths that do not match your current API catalog. Additionally, perform code scanning. Scan your source code repositories for references to deprecated endpoints. Often, the client-side code, such as the mobile app or frontend web app, still contains hard-coded links to old APIs.
Step 2: Traffic Correlation and Service Disruption
Once you identify a suspicious endpoint, for example, /api/v1/getUser, you need to know who is using it. Analyze the User-Agent to see if the traffic is coming from a legitimate legacy partner, an internal script, or a bot scanner.
If the source is unclear, you may need to employ “The Scream Test”. This is a controversial but effective tactic where you temporarily disable the endpoint for a short window, perhaps 30 minutes, during low-traffic hours. You then monitor your support tickets. If a critical business process breaks, you will hear a “scream” from the affected users. This quickly identifies the owner of the zombie traffic.
Step 3: Securing the Indispensable
You will inevitably find obsolete APIs that cannot be turned off. Perhaps they support a critical partner who refuses to upgrade, or a fleet of legacy IoT devices. If you cannot kill the endpoint, you must cage it.
This can be achieved through virtual patching. Use your WAF to apply strict rules to the legacy endpoint. For example, limit access to only the specific IP addresses of the known partners. Furthermore, enforce strict authentication. As detailed in our article on Certificate-Based Authentication for Users and Devices: A Comprehensive Security Strategy,6 the best way to secure a legacy endpoint is to mandate mutual TLS, or mTLS. Even if the API software itself is old and vulnerable, requiring a valid client certificate at the network layer prevents unauthorized attackers from even reaching the application.
Step 4: The Sunset Policy
Finally, establish a formal “Sunset Policy” to prevent future accumulation of unmanaged assets. This requires communicated timelines. When v2 is released, announce the End-of-Life (EOL) date for v1 immediately, such as stating “v1 will be deprecated in 12 months”.
Leading up to the EOL date, perform scheduled “brownouts” where the API intentionally fails for short periods by returning a 410 Gone error. This forces lazy developers to notice and migrate before the final cutoff.
The Governance Shift: From DevOps to DevSecOps
Successfully hunting obsolete APIs requires a cultural shift. The metrics for success in IT are often “uptime” and “speed of delivery”. We rarely reward teams for “amount of code deleted” or “number of APIs decommissioned”.
To solve this, organizations must integrate API governance into the earliest stages of the lifecycle. This concept, often called “Shift Left,” ensures that the plan for decommissioning an API is written before the API is even deployed. According to the OWASP API Security Top 10, “Improper Assets Management” is a governance failure, not a technical one. It occurs when there is a disconnect between the DevOps team who deploys and the SecOps team who protects. By bridging this gap with shared inventories and automated discovery tools, the creation of these vulnerabilities can be halted.
Conclusion
In the rush to innovate, we leave behind a trail of digital exhaust. Obsolete APIs are the technical debt that has come back to haunt the enterprise. They represent a massive, unmonitored attack surface that bypasses modern security investments. However, by treating API decommissioning as a core business process rather than an afterthought, leaders can close these backdoors. The strategy requires a mix of ruthless auditing, intelligent traffic analysis, and the courage to turn off systems that no longer serve the business. Security is not just about building walls; it is about cleaning up the mess inside them. A leaner, cleaner network is a secure network.
Secure Your Infrastructure with Emutare
Don’t let Zombie APIs haunt your network. Emutare empowers your organization to eliminate these invisible risks through comprehensive IT Asset and Patch Management. We help you gain total visibility and enforce robust Cybersecurity Governance to ensure no endpoint is left behind. Our expert Vulnerability Management services identify obsolete assets and security gaps before attackers exploit them. Partner with us to close the backdoors to your data and secure your digital ecosystem today.
References
- Verizon. (2024). 2024 Verizon Data Breach Investigations Report. https://www.verizon.com/business/resources/reports/2024-dbir-data-breach-investigations-report.pdf ↩︎
- Emutare. (2025). Secure CI/CD Pipelines: Design and Implementation. https://insights.emutare.com/secure-ci-cd-pipelines-design-and-implementation/ ↩︎
- Emutare. (2025). IoT Security Challenges in Enterprise Environments. https://insights.emutare.com/iot-security-challenges-in-enterprise-environments/ ↩︎
- Microsoft. Building a Comprehensive API Security Strategy. https://cdn-dynmedia-1.microsoft.com/is/content/microsoftcorp/microsoft/final/en-us/microsoft-brand/documents/Building-a-comprehensive-API-security-strategy.pdf ↩︎
- Open Web Application Security Project. OWASP API Security Project. https://owasp.org/www-project-api-security/ ↩︎
- Emutare. (2025). Certificate-Based Authentication for Users and Devices: A Comprehensive Security Strategy. https://insights.emutare.com/certificate-based-authentication-for-users-and-devices-a-comprehensive-security-strategy/ ↩︎
Related Blog Posts
- Adversarial Machine Learning: Understanding the Threats
- Selecting the Right Penetration Testing Partner: A Strategic Guide for Australian Organizations
- Digital Signatures: Implementation and Verification
- Code Review for Security: Techniques and Tools
- Secure Coding Guidelines for Multiple Languages: A Comprehensive Framework for Modern Software Development
- Mapping Security Controls to Business Requirements: A Strategic Approach to Cybersecurity Alignment
- GDPR Compliance for Australian Companies with EU Customers: A Comprehensive Guide for 2025

