There is a quiet crisis occurring in the heart of the modern Security Operations Center (SOC). It is not a crisis of technology, nor is it a crisis of funding. It is a crisis of human capital.
For years, the industry response to the evolving threat landscape has been additive. We have added more sensors, more logs, more dashboards, and more alerts. We have built towering stacks of security tools, assuming that more data equates to better protection. However, we failed to account for the primary processor of all that data: the human analyst.
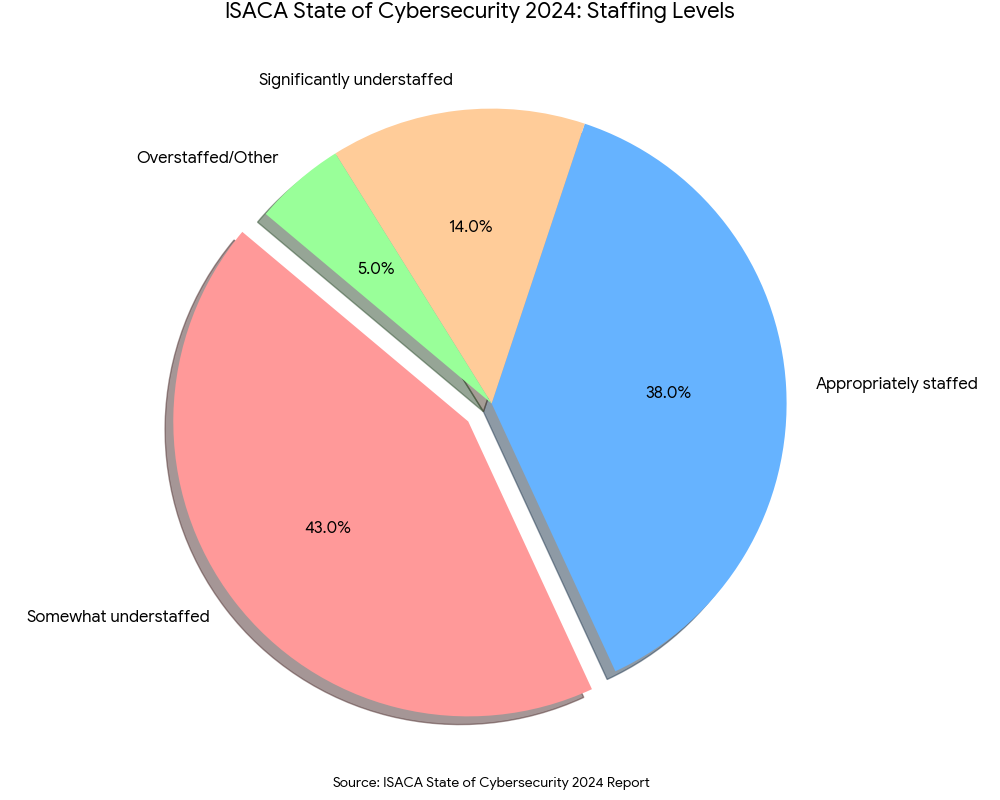
The result is a broken feedback loop. The influx of data has outpaced the human capacity to process it. According to the ISACA State of Cybersecurity 2024 Report,1 respondents who believe their team is somewhat understaffed are 43 percent, which is a three percentage point decrease from last year. A significant portion cites high stress levels as a primary reason for leaving the industry. We are not just losing the battle against adversaries; in many cases, we are losing our own people to burnout.
To build a sustainable security posture for 2025 and beyond, we must shift our focus from “more tools” to “better workflows.” We need to operationalize trust, not just between systems, but between the people managing them. This requires a holistic approach that tackles the root causes of cognitive overload: the invisibility of SaaS environments, the friction of communication, and the inability to measure strategic value.
1. The Cognitive Load of the Invisible Estate
The first crack in the feedback loop stems from the sheer complexity of the environment an analyst is expected to defend. In the past, the perimeter was defined and visible. Today, the perimeter is a sprawling web of Software-as-a-Service (SaaS) applications, many of which were procured without IT oversight.
For a SOC analyst, this “Shadow IT” creates a massive cognitive burden. They are often tasked with investigating anomalies in applications they do not administer, do not have logs for, and sometimes do not even know exist. When an alert fires regarding a suspicious login in a marketing automation tool, the analyst has to scramble to find context. Who owns this app? Is this behavior normal? Do we even have a license for this?
This lack of visibility is a primary driver of alert fatigue. It forces highly skilled professionals to spend their time chasing ghosts rather than hunting threats.
To regain control, organizations must implement rigorous governance over their cloud applications. As we discussed in our detailed guide on SaaS Security Posture Management for Critical Business Applications,2 the solution is not to ban SaaS usage, which would stifle business innovation, but to bring it into the light.
By utilizing automated Posture Management tools, security leaders can give their analysts a “single source of truth” regarding configurations and user privileges. This reduces the mental load significantly. Instead of asking “what is this app,” the analyst can immediately focus on “why is this configuration dangerous.”
According to the 2024 Splunk State of Security3 report, organizations that unified their visibility (by sharing data between Security, IT, and Engineering) saw a massive reduction in dwell time.The correlation is clear: when you remove the blind spots, you reduce the stress on the defender. Operationalizing trust begins with ensuring your team trusts the data they are looking at.
2. Breaking the “Swivel Chair” Fatigue with ChatOps
Once we have addressed the visibility of the estate, we must address the friction of the response.
A typical day for a Tier 1 or Tier 2 analyst involves an exhausting amount of context switching. They monitor a SIEM for alerts, switch to a ticketing system to log the incident, jump into an email client to contact a user, and log into a firewall interface to block an IP. This phenomenon, often called “swivel chair integration,” breaks the analyst’s flow state.3
Every time a human has to switch context, there is a “resumption lag” — a delay before they can fully focus on the new task.4 In a high-volume SOC, these lags accumulate into hours of lost productivity every week. Furthermore, this fragmented workflow isolates knowledge. One analyst might be working on a phishing ticket while another works on a related malware alert, unaware that they are looking at two sides of the same attack because their communications are siloed in different email threads.
The solution lies in meeting the workforce where they already are. This is the core philosophy behind ChatOps.
By integrating security tools directly into collaboration platforms like Slack or Microsoft Teams, we can centralize the workflow. As we explored in our article regarding ChatOps for Security Teams: Enhancing Collaboration,4 this approach does more than just save clicks. It creates a shared, real-time command center.
Imagine a scenario where a high-fidelity alert is posted automatically to a dedicated channel. The bot not only posts the alert but also pre-fetches the user’s active directory details and the reputation score of the suspicious IP. The analysts can discuss the threat in the thread, ensuring that all knowledge is captured in one place. More importantly, they can execute remediation actions, like suspending the compromised account, via a simple chat command.
Based on the SANS 2024 SOC Survey,5 automation and integration could be argued to be primary operational factors driving analyst retention. The report identifies manual repetition and ‘tool sprawl’ as the top barriers to SOC success; resolving these issues significantly reduces burnout and is credited with extending average analyst tenure to the 3–5 year mark. When you remove the drudgery of administrative toggling, you allow analysts to focus on the intellectual challenge of defense. That is how you fix the feedback loop. You make the technology serve the human, not the other way around.
3. Justifying the Human Investment
The third pillar of fixing the SOC feedback loop is economic. Burnout and turnover are expensive. Replacing a skilled security analyst can cost an organization upwards of 150% to 200% of their annual salary, once recruitment, onboarding, and ramp-up time are factored in.
However, many security leaders struggle to articulate this value proposition to the C-suite. They ask for more budget to hire more people, but they cannot prove the Return on Investment (ROI) of the team they currently have. This inability to justify resources leads to budget cuts, which leads to understaffing, which cycles back to burnout.
To break this cycle, we must get better at measuring and communicating the value of intelligence-driven operations.
We previously outlined a framework for this in our piece on Measuring ROI of Threat Intelligence Programs: A Strategic Framework for Australian Organizations.6 While the specific regional context may vary, the core principle is universal: value is not measured in “volume of activity” (e.g., tickets closed), but in “risk avoided.”
By arming your SOC with high-quality Threat Intelligence, you are essentially giving it a force multiplier. Instead of treating every alert with equal weight, intelligence allows the team to prioritize based on the actual threat landscape targeting your specific vertical.5
When you can demonstrate to the board that your team proactively patched a vulnerability because they received intelligence that it was being exploited in your sector, and that doing so prevented a potential loss of $2 million, you change the conversation. You are no longer asking for money to “keep the lights on.” You are demonstrating that your team is a strategic asset that protects the company’s bottom line.
This sense of purpose is vital for morale. Analysts do not burn out simply because they are busy; they burn out when they feel their work is futile.6 Connecting their daily tasks to high-level business value operationalizes a culture of purpose.
4. Implementation Guidance: The Human-Centric SOC
Transitioning to a human-centric SOC model is not something that happens overnight. It requires a deliberate restructuring of people, processes, and technology. Below is a practical roadmap for leaders looking to operationalize this trust and fix the broken feedback loop.
Phase 1: The Noise Audit (Weeks 1-4)
Before you can improve workflow, you must understand the current friction points.
- Analyze Ticket Volume: Look at the top 10 alert types your team handles. How many of them are false positives? How many are low-fidelity alerts from unmonitored SaaS applications?
- Shadow IT Discovery: Run a discovery scan to identify the unauthorized SaaS usage that is generating noise.7
- The “Stop Doing” List: Empower your team to identify tasks that add no value. If a specific report is never read or a specific alert is always ignored, turn it off.
Phase 2: The Integration Pilot (Weeks 5-12)
Start small with ChatOps to prove the concept.
- Select One Use Case: Do not try to migrate the entire SOC at once. Pick a high-volume, low-complexity use case, such as “Phishing Email Triage.”
- Build the Bot: Configure your collaboration platform to ingest these alerts. Ensure the bot enriches the data (e.g., checks the URL reputation) before alerting the humans.
- Measure the Delta: Track the Time to Acknowledge (TTA) and Time to Resolve (TTR) for this specific use case before and after the pilot. The efficiency gains are usually immediate and compelling.
Phase 3: The Intelligence Integration (Weeks 13+)
Shift from reactive to proactive.
- Feed Intelligence into Operations: Ensure your Threat Intelligence feeds are not just sitting in a portal but are integrated into the ChatOps workflow.
- Upskill the Team: Use the time saved from automation to train your analysts on threat hunting. Move them up the value chain.
- Report on Value: Change your monthly reporting to leadership. distinct from operational metrics (tickets closed), include a “Strategic Impact” section that highlights threats anticipated and risks mitigated.
5. The Role of Culture in Security Operations
Technology is the vehicle, but culture is the engine. A SOC equipped with the best SaaS security tools and the slickest ChatOps integrations will still fail if the culture is one of blame rather than curiosity.
In a “broken” feedback loop, an analyst who misses an alert is reprimanded. In a resilient feedback loop, the team asks: Why did the system fail to present this alert clearly? Was the analyst fatigued? Was the data buried?
By adopting the tools and strategies discussed, SaaS visibility, ChatOps collaboration, and Threat Intelligence, we create an environment where these questions can be answered constructively.
The “Psychological Safety” Factor
Google’s famous “Project Aristotle” found that psychological safety was the number one predictor of high-performing teams.8 This is doubly true in cybersecurity.
When we use ChatOps, we democratize knowledge, making it safe to ask questions in a public channel because the culture shifts from “hoarding knowledge” to “sharing context.”
When we implement SaaS Security Posture Management, we stop blaming users for “shadow IT” and start providing them with secure alternatives.
When we measure Threat Intel ROI, we stop valuing busy work and start valuing smart work.
Conclusion
The cybersecurity industry is at an inflection point. The strategies that got us here, hiring more bodies to watch more screens, are no longer viable. The volume of threats and the complexity of the digital estate have rendered the traditional SOC model obsolete.9
To thrive in this new era, we must fix the feedback loop. We must recognize that the most critical node in our network is the human analyst. By reducing their cognitive load through better visibility, streamlining their workflow through ChatOps, and validating their efforts through strategic intelligence, we can build a security operation that is not only robust but sustainable.
Operationalizing trust means creating a system where technology supports the people, enabling them to do what they do best: think, adapt, and defend.
Transform your SOC from a burnout factory into a proactive defense engine. Emutare helps you operationalize trust with targeted Cybersecurity Threat Intelligence and expert SIEM and XDR Deployment. We reduce the noise and cognitive load on your analysts through tailored Cybersecurity Consultation and AI-Driven Process Automation. Stop chasing ghosts and start validating strategic value. Let our team guide yours in building a sustainable, human-centric security posture that empowers your defenders to think, adapt, and succeed.
References
- Information Systems Audit and Control Association (ISACA). State of Cybersecurity 2024 Report. https://www.isaca.org/resources/reports/state-of-cybersecurity-2024 ↩︎
- Emutare. (2025). SaaS Security Posture Management for Critical Business Applications. https://www.isaca.org/resources/reports/state-of-cybersecurity-2024 ↩︎
- Splunk (2024). The State of Security 2024: The Race to Harness AI. https://www.splunk.com/en_us/form/state-of-security-2024.html ↩︎
- Emutare. (2025). ChatOps for Security Teams: Enhancing Collaboration. https://insights.emutare.com/chatops-for-security-teams-enhancing-collaboration/ ↩︎
- SANS. (2024). SANS 2024 SOC Survey. https://www.sans.org/white-papers/sans-2024-soc-survey-facing-top-challenges-security-operations ↩︎
- Emutare. (2025). Measuring ROI of Threat Intelligence Programs: A Strategic Framework for Australian Organizations. https://insights.emutare.com/measuring-roi-of-threat-intelligence-programs-a-strategic-framework-for-australian-organizations/ ↩︎
Related Blog Posts
- Data-Centric Security Architecture: Building Resilience Through Data-Focused Protection
- Network Security Zoning and Segmentation Design: Building Resilient Digital Perimeters in 2025
- Threat Intelligence Sharing: Communities and Frameworks
- Healthcare Information Security: Australian Privacy Requirements
- Cost-Effective Security Solutions for Limited Budgets
- Threat Hunting: Methodologies and Tools
- Email Data Loss Prevention Strategies: A Comprehensive Guide for Australian Organizations

