For the past decade, the cybersecurity industry has been obsessed with the human element. We run phishing simulations, enforce biometric checks, and mandate complex passwords for every employee. Yet, while we were busy locking the front door, the back wall was being dismantled by an army of ghosts.
In 2025, human users are a vast minority on enterprise networks. They are outnumbered by “Non-Human Identities” (NHIs), which include the service accounts, API keys, bots, containers, and serverless functions that keep modern infrastructure running.
Recent data from Entro Labs reveals a staggering statistic: NHIs now outnumber human identities by a ratio of 144 to 1. Even more concerning is that NHIs are growing at a rate of 44% year-over-year. These identities often possess privileged access, live forever without rotation, and are rarely monitored with the same rigor as their human counterparts.
For business leaders and IT professionals, this represents the single largest blind spot in the modern attack surface. This article explores why Non-Human Identity Management (NHIM) is the critical compliance challenge of 2026 and how to regain control of your invisible fleet.
The Multi-Cloud Complication
The explosion of NHIs is a direct byproduct of digital transformation. As organizations migrated to multi-cloud environments (AWS, Azure, Google Cloud), they moved away from monolithic applications toward microservices. In this architecture, every component needs an “identity” to talk to another. A database needs to trust a web server; a deployment script needs access to a cloud bucket; a monitoring tool needs to read logs.
The problem is fragmentation. In a single-cloud environment, identity management is difficult, but in a multi-cloud environment, it is chaotic. A “service account” in AWS behaves differently from a “managed identity” in Azure. Security teams often lack a unified view of these assets, leading to “Identity Sprawl.”
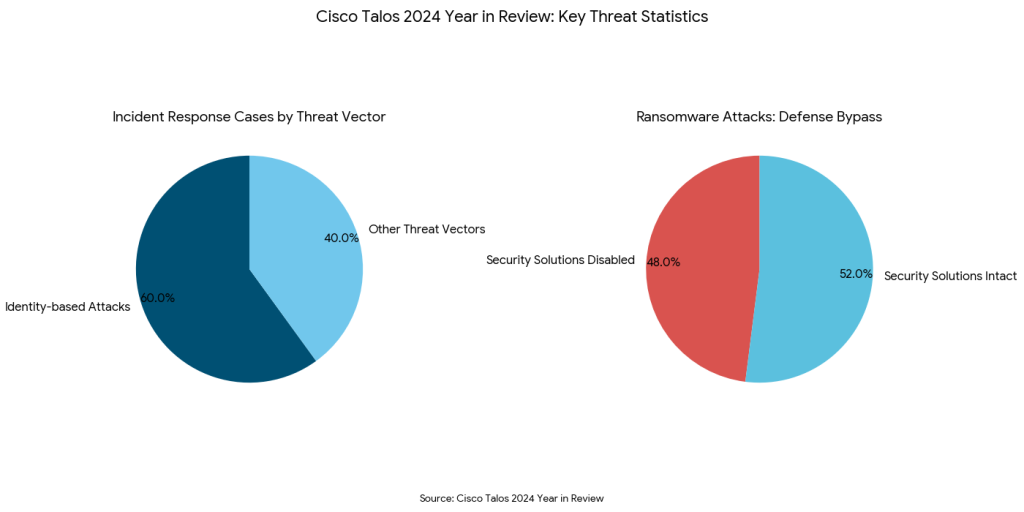
This visibility gap is precisely what attackers are exploiting. In their Cisco Talos 2024 Year in Review,1 Cisco Talos reported that identity-based attacks have become the dominant threat vector, accounting for 60% of all incident response cases. The report emphasizes a shift toward bypassing defenses, noting that ransomware actors successfully disabled security solutions in 48% of their attacks, further illustrating the move away from complex malware in favor of compromising existing system controls. Why hack a firewall when you can just find a hardcoded API key left in a public repository?
When an attacker compromises a human identity, the damage is usually limited to that user’s scope. When they compromise a machine identity, which is often granted “super-admin” privileges to ensure automation scripts don’t fail, they essentially gain the keys to the kingdom.
The Pipeline as a Factory of Risk
The birthplace of most non-human identities is the software development lifecycle. In the rush to release code faster, developers often embed secrets (API keys, passwords, certificates) directly into their code or CI/CD configurations.
To learn more about how to lock down this specific area, you can review our guide on Secure CI/CD Pipelines: Design and Implementation,2 which details how to scrub secrets from source code before they enter production.
However, even with clean code, the build pipeline itself relies on NHIs. Jenkins servers, GitHub Actions, and Docker containers all require identities to execute tasks. If these identities are not managed, they become “Zombie APIs,” which are deprecated but still active credentials that no one monitors.
Recent peer-reviewed research, Detecting Hard-Coded Credentials in Software Repositories via LLMs,3 indicates that hard-coded credentials remain a top-tier security vulnerability (CWE-798), persisting because of the immense difficulty in detecting embedded secrets across millions of lines of legacy code. The study highlights that despite known risks, the friction between rapid development cycles and complex secret management systems continues to drive high rates of credential exposure in modern repositories.
This “set it and forget it” mentality creates a permanent backdoor for attackers. Just as you revoke access for an employee who leaves the company, you must revoke the identity of a microservice that has been decommissioned. Unfortunately, in 2025, many organizations still lack the automated tooling to do this effectively.
The Certificate Solution
So, how do we secure an army of 144 machine identities for every one human? The answer is not more passwords. Passwords are static, shareable, and easily stolen. The gold standard for machine identity is Certificate-Based Authentication (CBA).
Unlike a static API key that might sit in a config file for three years, a digital certificate can be issued with a lifespan of minutes or even seconds. It relies on cryptographic trust rather than shared secrets.
As previously covered in our article on Certificate-Based Authentication for Users and Devices: A Comprehensive Security Strategy,4 implementing a robust Public Key Infrastructure (PKI) allows you to automate the issuance and rotation of these identities. If an attacker steals a certificate that expires in five minutes, the window of opportunity is drastically reduced compared to an API key that is valid forever.
The IoT Frontier
The challenge of NHIM extends beyond the cloud and into the physical world. Operational Technology (OT) and Internet of Things (IoT) devices are essentially physical machine identities.
From smart sensors in a manufacturing plant to connected HVAC systems in an office building, these devices need to authenticate themselves to the network. Historically, manufacturers shipped these devices with default passwords (e.g., “admin/admin”), creating massive security holes.
We discussed the implications of this in our analysis of IoT Security Challenges in Enterprise Environments.5 In 2026, best practice dictates that every IoT device should have a unique, immutable device identity (often a certificate burnt into a secure element) that is verified before it is allowed to transmit a single byte of data.
Strategic Defense: A Blueprint for 2026
To gain control over non-human identities, IT leaders must shift from a “detect and respond” model to a “governance and lifecycle” model. Here is a practical implementation guide:
1. Discovery and Inventory
You cannot secure what you cannot see. Use Cloud Infrastructure Entitlement Management (CIEM) tools to scan your multi-cloud environments. You will likely find thousands of “orphan” service accounts that are no longer in use. Many cloud non-human identities have no clear owner.
- Action: Audit all IAM roles in AWS, Azure, and GCP. Identify identities that haven’t authenticated in the last 90 days and disable them.
2. Enforce Least Privilege
Developers often grant “Admin” or “*” (wildcard) permissions to machine identities to avoid “permission denied” errors during testing. This is dangerous. Entro Labs in The NHI & Secrets Risk Report, H1 2025,6 reports that 1 in 20 AWS machine identities carries full-admin privileges.
- Action: Scrutinize the permissions of every service account. A script that backs up a database should only have “Read” access to that specific database, not “Write” access to the entire cloud storage bucket.
3. Automate Rotation
Static keys are the enemy. If you must use API keys or secrets, ensure they are rotated automatically.
- Action: Implement a Secrets Manager (like HashiCorp Vault or AWS Secrets Manager) so that applications retrieve credentials dynamically at runtime, rather than storing them in code.
4. Short-Lived Certificates
Move as many workloads as possible to certificate-based authentication with short lifespans.
- Action: Set up an internal Private CA (Certificate Authority) to issue certificates to your containers and microservices.
Conclusion
The ratio of 144:1 is not just a statistic; it is a signal that the fundamental nature of identity management has changed. For too long, security strategies have been anthropocentric, designed by humans, for humans.
In the multi-cloud era, the “user” is far more likely to be a piece of code than a person. Ignoring this reality leaves the vast majority of your network unmanaged and vulnerable. By treating machine identities with the same level of scrutiny as human employees, subjecting them to strict onboarding, least-privilege access, and mandatory offboarding, organizations can close the largest security gap of the decade.
The future of security isn’t just about who is logging in; it is about what is logging in.
Secure Your Invisible Fleet with Emutare
Don’t let Non-Human Identities become your largest blind spot. At Emutare, we bridge the gap between innovation and security with specialized services tailored for the multi-cloud era:
- Vulnerability Management: Identify “Zombie APIs” and orphan accounts across IT, OT, and IoT.
- Cybersecurity Governance: Implement robust frameworks to manage NHI lifecycles and ensure compliance.
- Infrastructure Architecture: Develop secure, certificate-based authentication environments.
- Advisory Services: Align your AI and automation adoption with expert risk management.
References
- Cisco Talos. (2025). Cisco Talos 2024 Year in Review. https://blog.talosintelligence.com/2024yearinreview/ ↩︎
- Emutare. (2025). Secure CI/CD Pipelines: Design and Implementation. https://Insights.emutare.com/secure-ci-cd-pipelines-design-and-implementation/ ↩︎
- Biringa, C., & Kul, G. (2025). Detecting hard-coded credentials in software repositories via LLMs. arXiv. https://arxiv.org/pdf/2506.13090v1 ↩︎
- Emutare. (2025). Certificate-Based Authentication for Users and Devices: A Comprehensive Security Strategy. https://Insights.emutare.com/certificate-based-authentication-for-users-and-devices-a-comprehensive-security-strategy/ ↩︎
- Emutare. (2025). IoT Security Challenges in Enterprise Environments. https://Insights.emutare.com/iot-security-challenges-in-enterprise-environments/ ↩︎
- Entro Labs. (2025). The NHI & Secrets Risk Report, H1 2025. https://23579664.fs1.hubspotusercontent-na1.net/hubfs/23579664/Assets/EL-The-NHI-Secrets-Risk-Report-H1-2025.pdf ↩︎
Related Blog Posts
- IoT Threat Modeling and Risk Assessment: Securing the Connected Ecosystem
- Red Team vs. Blue Team vs. Purple Team Exercises: Strengthening Your Organization’s Security Posture
- AI Security: Protecting Machine Learning Systems
- Common Penetration Testing Findings and Remediations
- Privacy Considerations in AI Systems: Navigating the Complex Landscape of Data Protection in the Age of Artificial Intelligence
- Threat Modeling for Application Security: A Strategic Approach to Modern Cybersecurity
- Cryptography Basics for IT Security Professionals: A Comprehensive Guide for Modern Cybersecurity

