In the race to plug every hole, organizations are drowning in complexity. Here is how to regain control
Imagine a construction site where every carpenter brings their own unique brand of hammer. One uses metric, one uses imperial, and another uses a proprietary digital hammer that requires a Wi-Fi connection. Individually, these tools are excellent. Collectively, they create chaos. The walls don’t align, the blueprints are ignored, and the house takes twice as long to build.
This is the current state of cybersecurity in many growing enterprises. It is a phenomenon known as “Tool Sprawl.”
For the past decade, the default response to a new cyber threat has been to buy a new tool. Phishing on the rise? Buy an email gateway. Endpoints vulnerable? Buy an EDR. Cloud issues? Buy a CSPM. Before long, the average Chief Information Security Officer (CISO) could find themselves managing a dashboard of 50 to 70 distinct security products, few of which communicate with one another. While the intention is to create an impenetrable fortress, the result is often the opposite: a fragmented defense that is expensive to maintain and surprisingly easy to breach. As noted in Breaking Alert Fatigue: AI-Assisted SIEM Framework for Effective Incident Response,1 Contemporary security information and event management (SIEM) solutions struggle to identify critical security incidents effectively due to the overwhelming number of false alerts generated by disparate security products, which results in significant alert fatigue and hinders effective incident response.
The Paradox of Accumulation
The logic seems sound on paper: more locks on the door should equal more safety. However, cybersecurity is not static; it is a dynamic ecosystem of data flow. When you introduce too many disparate tools, you introduce friction and blindness.
A landmark study by the Ponemon Institute2 revealed a startling statistic: organizations with more than 50 security tools were actually 8% less able to detect an attack than those with fewer tools. Why does this happen? The answer lies in complexity. Complexity is the enemy of security.
When a security team is bombarded by alerts from dozens of unintegrated platforms, they suffer from “alert fatigue.” They stop looking for the needle in the haystack because they are too busy trying to organize the hay.
The High Cost of the “Shiny Object” Syndrome
Tool sprawl usually stems from a reactive mindset. A new vulnerability hits the news, board members get nervous, and IT leadership feels pressured to “do something.” The quickest way to demonstrate action is to sign a purchase order.
However, this approach incurs three distinct types of debt:
1. Financial Debt
This is the most obvious cost. You are paying for licensing, support contracts, and renewal fees. But the hidden cost is in the overlap. It is common to find an organization paying for a standalone vulnerability scanner when their endpoint protection suite already has that feature built-in but turned off.
2. Operational Debt
Every tool requires a human to manage it. If you have 40 tools and a team of five, your team is not doing security; they are doing systems administration. They are patching the patch management server. They are resetting passwords for the dashboard. They are not hunting threats.
3. Cognitive Debt
This is the most dangerous. When data is siloed across different vendors, it becomes impossible to see the “story” of an attack. A firewall might see a ping, an antivirus might see a file download, and an identity provider might see a login. If those three tools don’t talk, no one sees the breach.
Architecture vs. Accumulation
The solution to tool sprawl is not necessarily to “delete everything.” It is to shift from a mindset of accumulation to one of architecture. You must stop buying products and start building a stack.
To learn more about how to structure this effectively, we recommend reviewing our guide on the Security Technology Stack for Growing Businesses.3
As discussed in that article, a healthy security stack is defined by how well the layers interact, not by how many layers there are. A lean stack where the Endpoint Detection and Response (EDR) feeds data directly into the Security Information and Event Management (SIEM) system is infinitely more powerful than a bloated stack where the tools are strangers to one another.
The Integration Imperative
A 2024 peer reviewed article by Deepa Ajish titled Streamlining Cybersecurity: Unifying Platforms for Enhanced Defense4 explains that many organizations are shifting toward fewer security vendors to improve how their defenses work together. The study notes that having too many disconnected tools leads to gaps in visibility, slower investigation, and heavier operational workloads. Consolidating security capabilities into a unified platform creates clearer oversight, stronger integration between controls, and smoother coordination during threat detection and response. Ajish concludes that consolidation is becoming a strategic approach to strengthening overall security posture rather than a budgeting decision.
When you consolidate, you reduce the attack surface. Every piece of software you install is code, and code has vulnerabilities. Ironically, security tools themselves can be the entry point for attackers if they are not patched or configured correctly. By reducing the number of agents running on your endpoints, you reduce the number of potential backdoors.
Optimizing What You Already Own
Before you buy the next “AI-powered” network appliance, you should ask a hard question: Are we fully using what we already have?
A classic example of this is the Intrusion Detection System (IDS). Many organizations deploy an IDS, set it to default, and then forget it. When it fails to catch a sophisticated attack, they blame the tool and buy a new one. In reality, the tool was fine; the deployment strategy was the failure.
As previously covered, effective security is about tuning and placement. You can gain significant insights by reading our deep dive into IDS/IPS Deployment Strategies for Maximum Effectiveness.5
By refining the rules of your existing IDS and ensuring it is inspecting internal “East-West” traffic (not just the perimeter), you can often achieve the visibility you thought you needed a new tool to provide. Optimization almost always beats acquisition.
Risk-Based Rationalization
How do you decide which tools to keep and which to cut? You cannot do it by looking at the price tag. You must do it by looking at the risk.
Many tools are purchased to mitigate risks that are theoretically possible but practically unlikely for your specific business. If you are a retail business with no proprietary intellectual property, do you need the same heavy-duty Data Loss Prevention (DLP) solution as a defense contractor? Probably not.
This requires a strategic pivot to Risk-Based Vulnerability Prioritization. Instead of trying to fix every theoretical hole with a tool, you focus on the vulnerabilities that actually threaten your business critical assets.
To learn more about filtering out the noise, refer to our article on Risk-Based Vulnerability Prioritization: A Strategic Approach to Modern Cybersecurity.6
When you prioritize by risk, the tool set clarifies itself. You keep the tools that protect your “Crown Jewels” and you ruthless retire the tools that are guarding empty rooms.
The Role of the “Platform” Approach
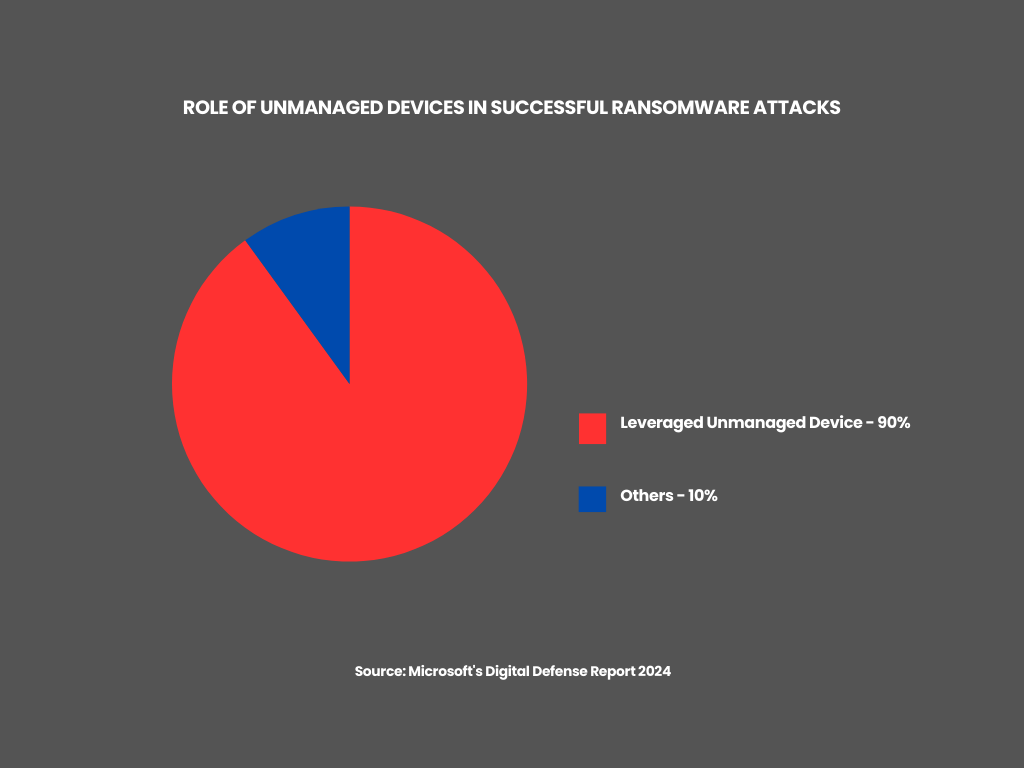
The market is shifting. According to Microsoft’s Digital Defense Report 2024,7 the inability to see and monitor the entire attack surface is not just an operational nuisance; it is the primary enabler of modern cyberattacks. Fragmentation leads to “unmanaged” pockets of the network, and it found that in more than 90% of successful ransomware attacks, the attacker leveraged an unmanaged device. Whether used as the initial open door or as a ‘safe haven’ to launch encryption without detection, these fragmented, unmonitored assets are the common denominator in nearly every major breach. In response, major vendors are moving toward “platforms.”
A platform approach means buying a suite of tools from a single ecosystem (like Microsoft, Palo Alto, or Cisco) rather than “best of breed” point solutions.
In the past, “best of breed” was the gold standard. You wanted the absolute best antivirus, the absolute best firewall, and the absolute best email filter, regardless of who made them. Today, “best of suite” is often the superior strategy. A “good enough” antivirus that shares telemetry natively with your firewall is better than a “perfect” antivirus that isolates data.
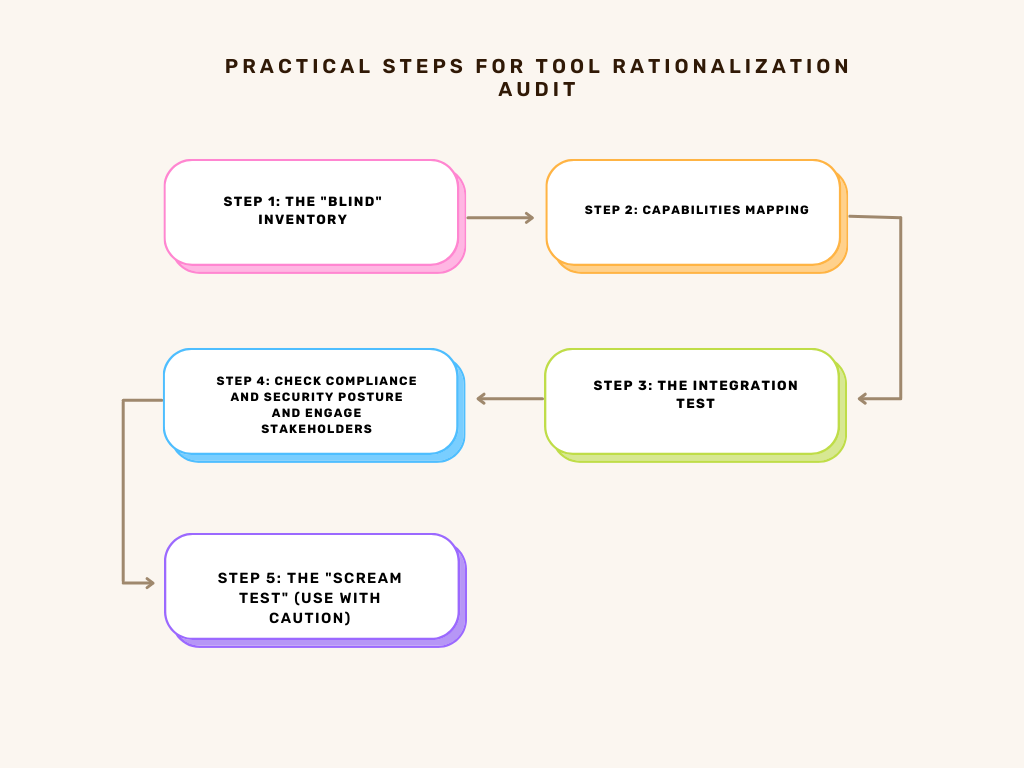
Practical Guidance: The Tool Rationalization Audit
If you suspect your organization is caught in the tool sprawl trap, here is a practical, four-step process to dig your way out.
Step 1: The “Blind” Inventory
Ask your finance team for a list of all software payments categorized under “Security” or “IT Infrastructure.” Then, ask your IT team for a list of all security tools they use.
Compare the lists. You will almost certainly find tools that are being paid for but not used (Shelfware), or tools that are being used but IT didn’t know about (Shadow IT).
Step 2: Capabilities Mapping
Create a simple spreadsheet. In the first column, list your security needs based on a framework like NIST (Identify, Protect, Detect, Respond, Recover). In the next columns, map your tools to these needs.
- Example: “Endpoint Protection.”
- Tool A: Does this.
- Tool B: Also does this.
- Tool C: Has a module for this.
If you find three tools covering the same square on the spreadsheet, you have found your redundancy.
Step 3: The Integration Test
For every tool on your list, ask: “Does this tool automatically send data to my central dashboard (SIEM/SOAR)?”
If the answer is “No,” mark it in red. A standalone tool is a liability. Unless it serves a highly specialized, isolated function, it should be on the chopping block.
Step 4: Check Compliance and Security Posture and Engage Stakeholders
Verify that each tool meets organizational security policies and compliance mandates, including data handling and audit requirements.
Involve end-users, IT teams, and management to gather diverse perspectives on tool effectiveness and challenges
Step 5: The “Scream Test” (Use with Caution)
Once you have identified a redundant tool, don’t renew the license. Or, if it is an internal deployment, turn it off for a week (after getting approval). If no one complains and no critical processes break, you have just proved that the tool was unnecessary.
The Human Element: Protecting Your Team
Finally, we must address the human cost. Cybersecurity talent is rare. A report by ISC2 (The International Information System Security Certification Consortium) consistently highlights the global workforce gap in cybersecurity.
When you burden your scarce talent with managing 50 different consoles, you burn them out. They leave for companies that have streamlined stacks. By consolidating your tools, you are not just cleaning up your network; you are improving the quality of life for your analysts. You are freeing them from the drudgery of maintenance so they can focus on the creativity of defense.
Conclusion
The era of “buying safety” is over. We are now in the era of managing safety.
Security is not a shopping list. It is a discipline. The most secure organizations are not the ones with the biggest budgets or the most logos on their architecture diagrams. They are the ones with the clearest visibility and the most integrated workflows.
It is time to stop adding and start subtracting. Look at your stack. Look at your risks. And have the courage to say “no” to the next shiny tool, so you can say “yes” to a more resilient, manageable, and secure future.
Stop drowning in disconnected dashboards. Emutare helps you shift from accumulation to architecture by streamlining your defense stack. We specialize in Cybersecurity and IT Infrastructure Architecture Development and unified SIEM & XDR Deployment to ensure your tools work together, not against each other. Through our strategic Cybersecurity Advisory and Risk Assessments, we help you identify redundancies, prioritize critical vulnerabilities, and maximize the value of your existing assets.
References
- Ban, T., Takahashi, T., Ndichu, S., & Inoue, D. (2023). Breaking alert fatigue: AI-assisted SIEM framework for effective incident response. Applied Sciences, 13(11), 6610. https://www.mdpi.com/2076-3417/13/11/6610 ↩︎
- Ponemon Institute. (2020). Cyber Resilient Organization Report 2020. https://riskcue.id/uploads/ebook/20210819081636-2021-08-19ebook081207.pdf ↩︎
- Emutare. (2025). Security Technology Stack for Growing Businesses. https://insights.emutare.com/security-technology-stack-for-growing-businesses/ ↩︎
- Ajish, D. (2024). Streamlining cybersecurity, unifying platforms for enhanced defense. International Journal of Information Technology, Research and Applications, 3(2), 48 to 57. https://ijitra.com/index.php/ijitra/article/view/106/70 ↩︎
- Emutare. (2025). IDS/IPS Deployment Strategies for Maximum Effectiveness. https://insights.emutare.com/ids-ips-deployment-strategies-for-maximum-effectiveness/ ↩︎
- Emutare. (2025). Risk-Based Vulnerability Prioritization: A Strategic Approach to Modern Cybersecurity. https://insights.emutare.com/risk-based-vulnerability-prioritization-a-strategic-approach-to-modern-cybersecurity/ ↩︎
- Microsoft. (2024). Microsoft Digital Defense Report 2024. https://cdn-dynmedia-1.microsoft.com/is/content/microsoftcorp/microsoft/final/en-us/microsoft-brand/documents/Microsoft%20Digital%20Defense%20Report%202024%20%281%29.pdf ↩︎
Related Blog Posts
- Continuous Compliance Monitoring Through Automation
- Comprehensive Security for Remote Workforces: Safeguarding the Distributed Enterprise
- Advanced Anti-Phishing Controls and User Training: Building Resilient Cybersecurity Defenses
- Board Reporting on Cybersecurity: What Executives Need to Know
- Multi-Factor Authentication: Comparing Different Methods
- Secrets Management in DevOps Environments: Securing the Modern Software Development Lifecycle
- Zero Trust for Remote Work: Practical Implementation

